You could have observed a slight drop within the quantity of protection of ransomware on our Kaspersky Each day weblog lately. Sadly, it’s not that ransomware assaults have stopped. Removed from it — such incidents at the moment are so commonplace that they’ve change into a part of the cyber-furniture. Nonetheless, some ransomware assaults nonetheless have the facility to shock. On this put up, we take you thru the ransomware incidents of 2024 that made a long-lasting impression by way of scale, influence, or mode of assault…
January 2024: ransomware assault on Toronto Zoo
One of many first main ransomware incidents of 2024 was the January assault on Canada’s greatest zoo, situated in Toronto. The zoo’s administration was fast to reassure the general public that no programs associated to animal care had been impacted. Certainly, its web site and ticketing service had been additionally unaffected, so the zoo continued to welcome guests as typical.
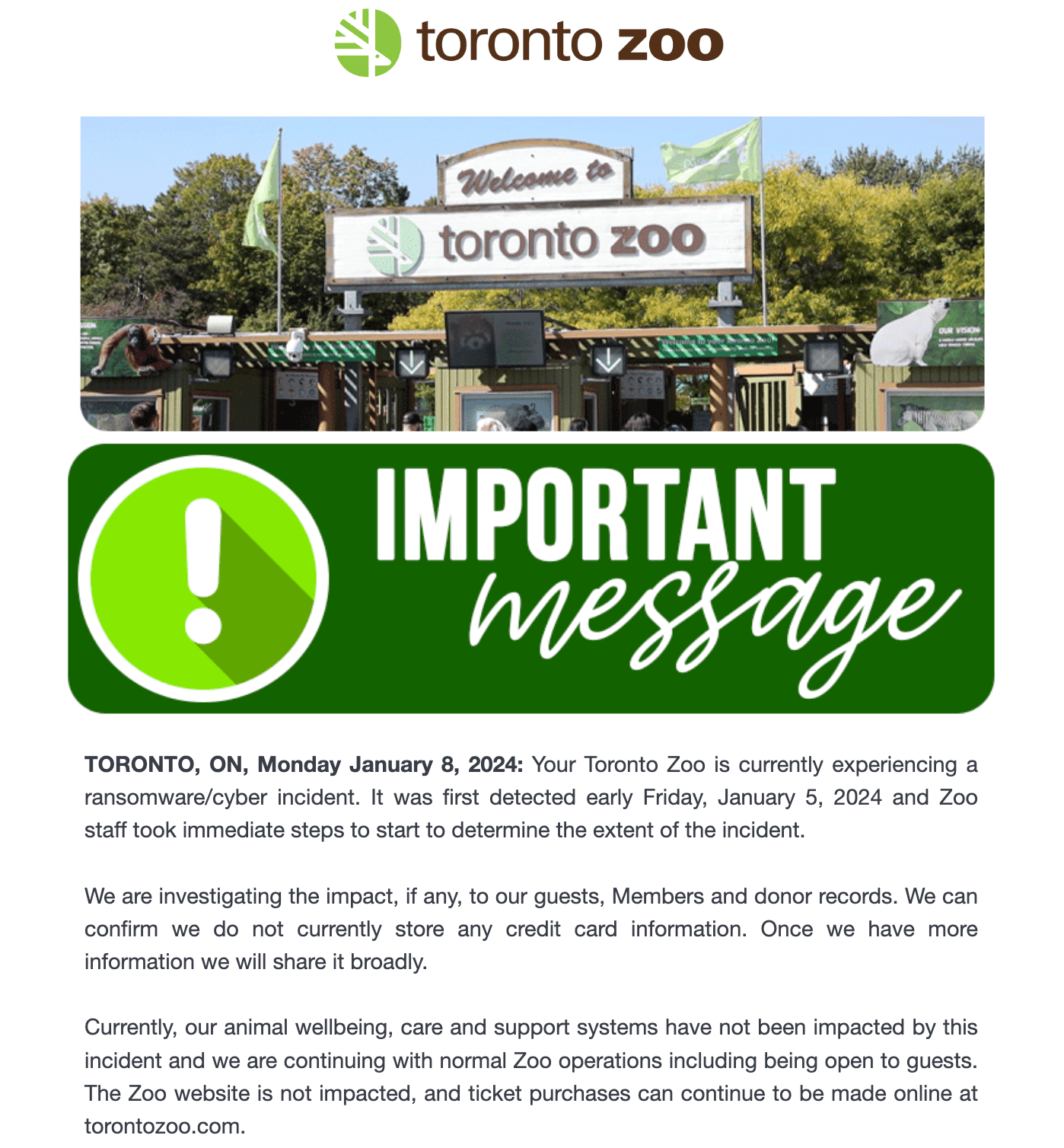
The official Toronto Zoo web site experiences a cyberattack and assures that every one animals are positive. Supply
It quickly transpired that the attackers had stolen a big quantity of zoo staff’ private info — courting again to 1989. This incident served as one more reminder that even organizations far faraway from vital sectors can change into targets of ransomware assaults.
February 2024: $3.09 billion assault on UnitedHealth
February’s assault on the U.S. healthcare insurance coverage big UnitedHealth would simply declare the “ransomware incident of the yr” award if such existed. The assault was in actual fact carried out on Optum Perception, a UnitedHealth subsidiary that gives technology-enabled providers.
Getting granular right here, the direct goal was Change Healthcare, which has been a part of Optum since 2022. This firm’s platform serves as a monetary middleman between payers, sufferers, and healthcare suppliers. The assault took down over 100 completely different Optum digital providers. Because of this, UnitedHealth was in a position to course of neither digital funds nor medical functions. Basically, the corporate couldn’t carry out its core operate — inflicting chaos throughout the U.S. healthcare system.
The assault’s repercussions had been so intensive that UnitedHealth even arrange a devoted web site to supply updates in regards to the technique of restoring the corporate’s affected IT programs. The majority of the restoration work was carried out within the first months after the assault. Nevertheless, nearly a yr on, the location continues to put up common updates, and a few programs nonetheless have the “service partially obtainable” standing.
A couple of days after the assault, the ransomware gang BlackCat/ALPHV claimed accountability. As well as, they reported stealing 6TB of confidential information — together with medical data, monetary paperwork, private information of U.S. civilians and army personnel, and a wealth of different delicate info.
UnitedHealth ended up paying the gang a $22 million ransom. And it’s rumored that the corporate needed to pay up once more when BlackCat’s accomplices from the RansomHub group claimed they hadn’t acquired their share and commenced leaking the stolen information into the general public area.
Nevertheless, in comparison with the whole monetary losses attributable to the incident, the ransom was a mere drop within the ocean. UnitedHealth’s personal monetary experiences estimate the harm in Q1 alone at $872 million. As for the whole harm for the yr 2024, it reached an eye-watering $3.09 billion.
In accordance with the newest experiences, the attackers stole medical information of greater than 100 million sufferers, which is roughly one in three U.S. residents!
March 2024: Panera Bread’s week-long outage
In March, ransomware attackers focused U.S. food-chain big Panera Bread. The incident knocked out lots of its IT programs, together with the web ordering service, offline fee system, telephony, web site and cellular apps, loyalty program, varied inner programs for workers, and different providers.
Stub message on the Panera Bread web site. Supply
Over 2000 eating places within the Panera Bread chain continued to function after the assault — however in stone-age circumstances: fee was by money solely; subscription gives (equivalent to limitless drinks for $14.99 per 30 days) had been briefly unavailable; loyalty program factors weren’t awarded; and restaurant workers needed to manually coordinate their work schedules with managers. The outage lasted a few week.
Throughout the assault, as we realized three months later, the non-public information of Panera Bread staff was stolen. By the seems of it, the corporate ended up paying a ransom to maintain that information from being printed.
April 2024: Hunters Worldwide assault on Hoya Company
Early April noticed an assault on Hoya Company, the foremost Japanese optics producer. In an official assertion, the corporate mentioned that the programs of some manufacturing vegetation, plus the ordering system for a number of merchandise had been affected.
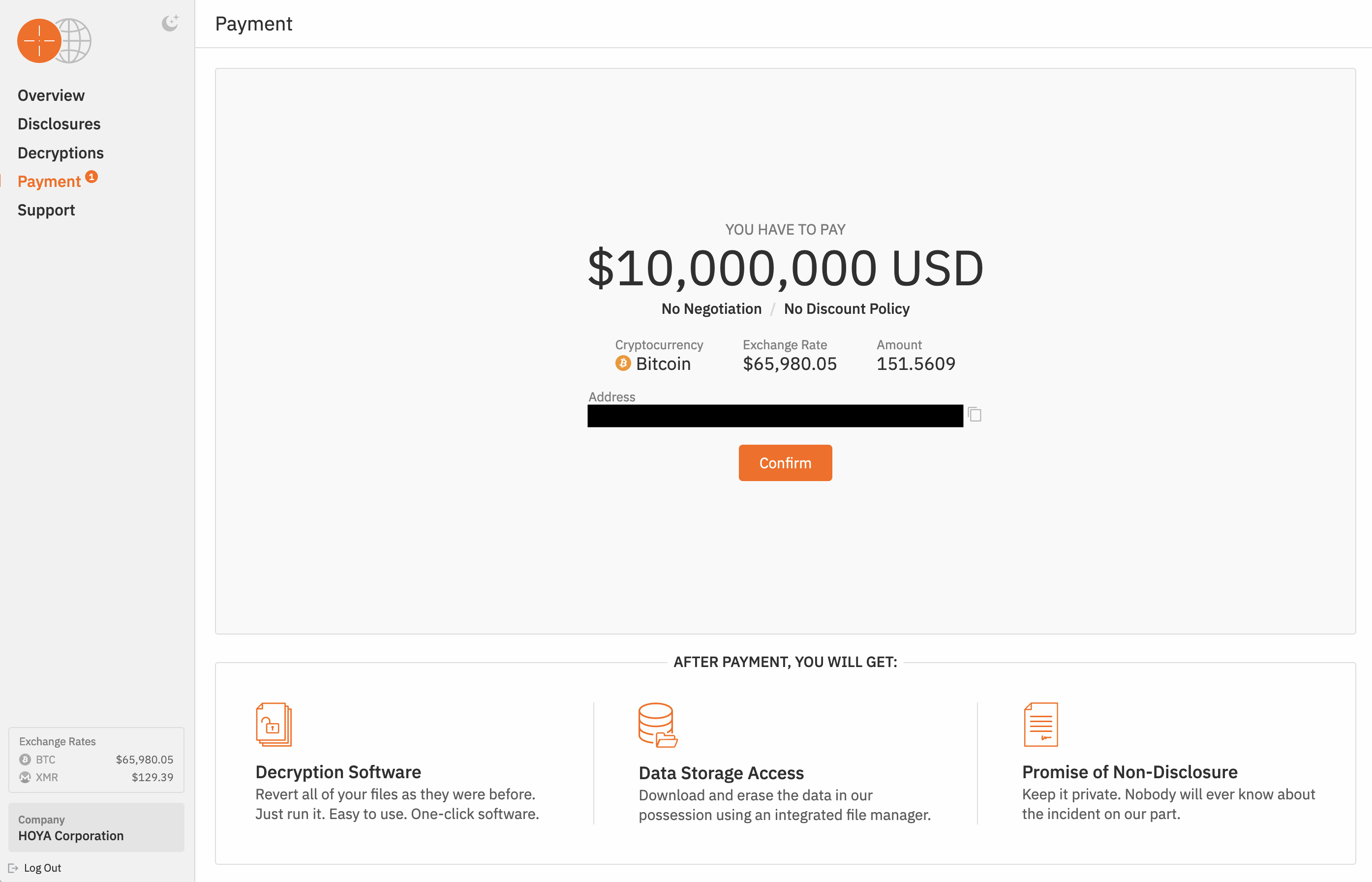
Hunters Worldwide demanded a ransom of $10 million (151.56 BTC on the then change price) from Hoya Company. Supply
Every week after the incident, it was confirmed as a ransomware assault. The Hunters Worldwide ransomware-as-a-service group’s web site reported that the attackers had stolen 1.7 million information from Hoya (round 2TB), and demanded a ransom of $10 million.
Could 2024: Main disruptions at U.S. healthcare community Ascension
In early Could, Ascension, one of many largest healthcare networks in the US, had a few of its programs taken offline because of a “cybersecurity occasion”. The “occasion” in query was quickly revealed to be a ransomware assault on the group’s IT infrastructure. The disruption affected digital medical data, telephony, and programs for ordering exams, procedures, and medicines.
Because of this, some hospitals run by Ascension couldn’t admit emergency sufferers, and needed to divert ambulances to different services. Healthcare staff additionally reported having to modify to pen and paper and writing out medical referrals from reminiscence.
Restoring the affected digital programs took over a month. The Black Basta ransomware group claimed accountability for the assault. The investigation revealed that the foundation reason behind the assault was an worker who downloaded a malicious file onto an organization system.
It was revealed in late 2024 that the cybercriminals had stolen the non-public information of 5.6 million sufferers and hospital workers. This information included medical data, fee particulars, insurance coverage info, social safety and ID numbers, addresses, dates of beginning, and extra. As compensation, Ascension supplied all these affected a free two-year subscription to its identity-theft safety service.
June 2024: Ransomware assault on healthcare supplier hits London hospitals
In early June, information broke of a ransomware assault on Synnovis, a UK firm offering pathology and diagnostic providers to a number of main London hospitals. Because of this, over 800 surgical procedures had been canceled and a few sufferers diverted to different services.

Main outage reported on the web site of Synnovis, a healthcare supplier for a number of main London hospitals. Supply
One of many worst penalties of the assault was that medical doctors had been unable to match donor and affected person blood varieties, forcing them to make use of the common blood kind O. This shortly led to a scarcity.
July 2024: Los Angeles County Superior Courtroom shut down by ransomware
The Los Angeles County Superior Courtroom, the biggest single unified trial court docket in the US, suspended all 36 courthouses within the county because of a ransomware assault. Each exterior providers (such because the court docket’s web site and the jury responsibility portal) and inner sources (together with the case administration system) had been impacted.
The Los Angeles courts reopened two days later, however restoring publicly-accessible digital providers took a few week longer. After that, nonetheless, the Superior Courtroom stopped updating the general public in regards to the incident, so it’s unknown how lengthy it took to revive the courts’ inner programs. It additionally stays a thriller whether or not the court docket paid a ransom or what information the attackers could have gotten away with.
August 2024: Ransomware assault on vodka maker Stoli
In August, a ransomware assault focused Stoli Group, the producer of Stolichnaya vodka and a number of different drinks. The incident had a severe influence on the corporate’s IT infrastructure and operations: an ERP system failure meant that every one inner processes, together with accounting, needed to be transferred to guide mode.
Specifically, the incident meant that Stoli Group firms couldn’t submit monetary statements to collectors — which alleged that the Stoli firms didn’t repay a debt of $78 million. Stoli Group needed to file for chapter in December.
September 2024: Highline Public Faculties closure because of ransomware
In early October, Highline Public Faculties, a public faculty district within the U.S. state of Washington, briefly closed all 34 of its member colleges, which serve greater than 17,000 college students and make use of round 2000 workers. The cyberattack halted all academic actions, together with sports activities occasions and conferences, for 4 faculty days.
A couple of month after the incident, Highline’s administration confirmed that the assault was ransomware-related. Sadly, Highline Public Faculties officers by no means disclosed whether or not any private info of workers or college students had been compromised. As a precaution, nonetheless, the district supplied all Highline staff one yr of free credit score and identification monitoring providers.
Though the colleges had been fairly fast to reopen, it took a very long time to revive the IT infrastructure again to regular operation. Regretfully, greater than a month handed earlier than staff and college students had been lastly urged to alter their passwords and reinstall the working system on all school-supplied gadgets.
October 2024: Ransomware assault on Casio
In early October, Japan’s Casio, the famend electronics producer, reported unauthorized entry to its community. In accordance with its assertion, the incident resulted in failure of IT programs and unavailability of sure unspecified providers.
5 days later, the ransomware group Underground claimed accountability for the assault. The group additionally stole information through the hack, which it posted on its web site — together with confidential paperwork, patent info, staff’ private information, authorized and monetary paperwork, challenge info, and so forth. The very subsequent day, Casio confirmed the information theft.
In early 2025, Casio launched extra particulars in regards to the variety of folks whose information had been stolen. In accordance with the corporate, a complete of 8500 folks had been affected, of which round 6500 had been staff, and 2000 had been enterprise companions. On the identical time, Casio reported not paying a ransom to the attackers and introduced that almost all (however not all) providers had been already again up and working.
Apparently, in that very same October 2024, Casio was the sufferer of one other profitable assault, unrelated to the above ransomware incident.
November 2024: Ransomware assault on Bologna FC
In November, ransomware claimed a moderately atypical sufferer — the Italian soccer membership Bologna FC. The membership posted on its web site an official assertion a few ransomware assault, warning that “it’s a severe prison offence” to retailer or distribute stolen information.
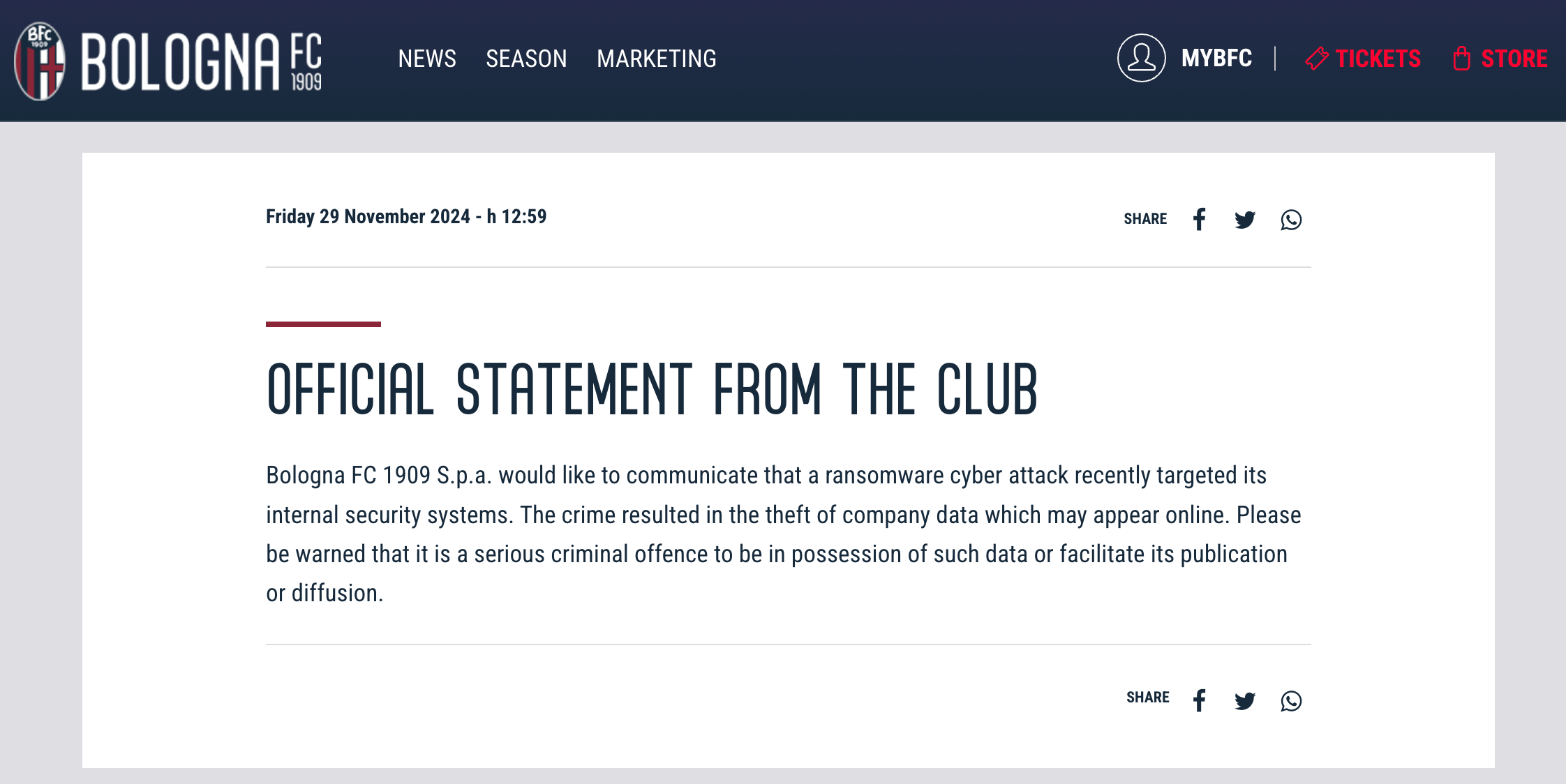
The Italian soccer membership Bologna FC web site experiences a ransomware assault. Supply
The RansomHub group claimed accountability for the hack. Later, it printed the stolen information after the membership refused to pay the ransom. In accordance with the attackers, the leaked info included sponsorship contracts, the membership’s full monetary historical past, private and confidential participant information, medical data, switch methods, confidential information of followers and membership staff, and rather more.
December 2024: Ransomware assaults medical tissue and tools provider Artivion
In December, Artivion, a world provider of tissues and tools for cardiac surgical procedure, introduced that its IT infrastructure had been compromised by a cyberattack. The attackers encrypted a number of the firm’s programs and stole information from affected computer systems.
In accordance with Artivion, the incident prompted “disruptions to some order and delivery processes”, in addition to company operations. The corporate additionally reported being insured in opposition to such incidents, however the coverage could not totally cowl the harm attributable to the assault.
The best way to defend in opposition to ransomware assaults
Ransomware continues to evolve, and yearly the assaults tackle new, complicated kinds. Subsequently, in at the moment’s world, efficient safety in opposition to ransomware requires a complete method. We suggest the next safety measures:



