Sooner or later, the knowledge safety division of any giant firm inevitably begins to think about introducing a SIEM system — or changing the prevailing one, and should due to this fact estimate the finances required for its deployment. However SIEM isn’t a light-weight product that may be deployed inside current infrastructure. Nearly all options on this class require further {hardware}, that means that tools should be bought or rented.
So, for correct budgeting, it’s essential to bear in mind the anticipated {hardware} configuration. On this publish, we focus on how SIEM {hardware} necessities change relying on the corporate’s profile and system’s structure, and supply tough parameters to assist estimate the preliminary price of such tools.
Evaluating the info movement
Primarily, a SIEM system collects occasion information from inner and exterior sources and identifies safety threats by correlating this information. Subsequently, earlier than contemplating what {hardware} can be required, it’s important to first assess the quantity of data the system will course of and retailer. To this finish, it is advisable to first establish important dangers to the infrastructure, after which decide the info sources that should be analyzed to assist detect and tackle threats associated to those dangers. These are the info sources to deal with. Such an evaluation is critical not solely to find out the required {hardware}, but additionally to estimate the price of licensing. For instance, the price of licensing for our Kaspersky Unified Monitoring and Evaluation Platform SIEM system immediately depends upon the variety of occasions per second (EPS). One other vital facet is to examine how the seller calculates the variety of occasions for licensing. In our case, we take the occasions per second after filtering and aggregation, calculating the common variety of occasions over the previous 24 hours slightly than their peak values — however not all distributors observe this method.
The commonest sources embrace endpoints (Home windows occasions, Sysmon, PowerShell logs, and antivirus logs), community units (firewalls, IDS/IPS, switches, entry factors), proxy servers (equivalent to Squid and Cisco WSA), vulnerability scanners, databases, cloud methods (equivalent to AWS CloudTrail or Workplace 365), and infrastructure administration servers (area controllers, DNS servers, and so forth).
As a rule, to type preliminary expectations concerning the common occasion movement, the dimensions of the group can function a information. Nonetheless, the architectural particularities of particular IT infrastructure could make firm measurement a much less decisive parameter.
Normally, for small and medium-sized organizations with only one workplace — or as much as a number of workplaces with good communication channels amongst them and IT infrastructure positioned in a single information middle — a mean occasion movement of 5000–10 000 EPS may be anticipated. For giant corporations, making an estimate is more difficult: relying on the complexity of the infrastructure and the presence of branches, EPS can vary from 50 000 to 200 000 EPS.
Architectural parts of an SIEM system
An SIEM system typically consists of 4 primary parts: the administration subsystem, occasion assortment subsystem, correlation subsystem, and storage subsystem.
Core (administration subsystem). You’ll be able to consider this because the management middle of the system. It permits managing the opposite parts, and gives visualization instruments for SOC analysts — enabling them to simply configure operational parameters, monitor the SIEM system’s state, and, most significantly, view, analyze, kind and search occasions, course of alerts, and work with incidents. This management middle must additionally help log viewing via widgets and dashboards, and allow fast information search and entry.
The core is an integral part and may be put in as a single occasion or as a cluster to supply the next stage of resilience.
Occasion assortment subsystem. Because the identify suggests, this subsystem collects information from numerous sources and converts it right into a unified format via parsing and normalization. To calculate the required capability of this subsystem, one should take into account each the occasion movement depth and the log format through which occasions arrive from sources.
The server load depends upon how the subsystem processes logs. For instance, even for structured logs (Key Worth, CSV, JSON, XML), you should use both common expressions (requiring considerably extra highly effective {hardware}) or the seller’s built-in parsers.
Correlation subsystem. This subsystem analyzes information collected from logs, identifies sequences described in correlation rule logic, and, if obligatory, generates alerts, determines their risk ranges, and minimizes false positives. It’s vital to keep in mind that the correlator’s load can also be decided not solely by the occasion movement however by the variety of correlation guidelines and the strategies used to explain detection logic as properly.
Storage subsystem. An SIEM system should not solely analyze but additionally retailer information for inner investigations, analytics, visualization and reporting, and in sure industries — for regulatory compliance and retrospective alert evaluation. Thus, one other important query on the SIEM system design stage is how lengthy you wish to retailer collected logs. From an analyst’s perspective, the longer the info is saved, the higher. Nonetheless, an extended log retention interval will increase {hardware} necessities. A mature SIEM system gives the flexibility to strike a steadiness by setting completely different retention durations for various log varieties. For instance, 30 days for NetFlow logs, 60 days for Home windows informational occasions, 180 days for Home windows authentication occasions, and so forth. This enables information to be optimally allotted throughout out there server sources.
It’s additionally vital to know what quantity of information can be saved utilizing scorching storage (permitting fast entry) and chilly storage (appropriate for long-term retention). The storage subsystem should provide excessive efficiency, scalability, cross-storage search capabilities (each cold and warm), and information viewing choices. Moreover, the flexibility to again up saved information is important.
Architectural options of Kaspersky SIEM
So, we’ve laid out the perfect necessities for an SIEM system. It most likely gained’t shock you that our Kaspersky Unified Monitoring and Evaluation Platform meets these necessities. With its built-in functionality to scale for information flows reaching lots of of 1000’s of EPS inside a single occasion, our SIEM system isn’t afraid of excessive hundreds. Importantly, it doesn’t have to be break up into a number of cases with correlation outcomes reconciled afterwards — not like many different methods.
The occasion assortment subsystem of the Kaspersky Unified Monitoring and Evaluation Platform system is provided with a wealthy set of parsers optimized for processing logs in every format. Moreover, the multi-threading capabilities of Go imply the occasion movement may be processed utilizing all out there server sources.
The info storage subsystem utilized in our SIEM system consists of servers that retailer information, and servers with the clickhouse-keeper position, which handle the cluster (these servers don’t retailer information themselves however facilitate coordination amongst cases). For information flows of 20 000 EPS with a comparatively low variety of search queries, these providers can function on the identical servers that retailer the info. For increased information flows, it’s advisable to separate these providers. For example, they are often deployed on digital machines (a minimal of 1 is required, although three are advisable).
The Kaspersky Unified Monitoring and Evaluation SIEM storage system is versatile — permitting occasion flows to be distributed throughout a number of areas, and specifying the storage depth for every area. For instance, cheap disks can be utilized to create chilly storage (the place searches are nonetheless potential, simply slower). This chilly storage can home information that’s unlikely to require evaluation however should be saved as a consequence of regulatory necessities. Such info may be moved to chilly storage actually the day after it’s collected.
Thus, the info storage method carried out in our SIEM system allows long-term information retention with out exceeding the finances on costly tools, due to cold and warm storage capabilities.
SIEM structure deployment utilizing our SIEM for example
The Kaspersky Unified Monitoring and Evaluation Platform helps a number of deployment choices, so it’s vital first to find out your group’s structure wants. This may be finished based mostly on the estimated EPS movement, and the particularities of your organization. For simplicity, let’s assume the required information retention interval is 30 days.
Information movement: 5000–10 000 EPS
For a small group, the SIEM system may be deployed on a single server. For instance, our SIEM system helps the All-in-One set up possibility. On this case, the required server configuration is 16 CPUs, 32GB of RAM, and a 2.5TB of disk area.
Information movement: 30 000 EPS
For bigger organizations, separate servers are wanted for every SIEM element. Dedicating a server solely for storage ensures that search queries don’t have an effect on the processing of occasions by the collector and correlator. Nonetheless, the collector and correlator providers can nonetheless be deployed collectively (or individually, if desired). An approximate tools configuration for this situation is as follows:
- Core: 10 CPUs, 24GB of RAM, 0.5TB of disk area
- Collector: 8 CPUs, 16GB of RAM, 0.5TB of disk area
- Correlator: 8 CPUs, 32GB of RAM, 0.5TB of disk area
- Storage: 24 CPUs, 64GB of RAM, 14TB of disk area
Information movement: 50 000–200 000 EPS
For giant enterprises, further elements should be thought of when defining the structure. These embrace guaranteeing resilience (because the substantial data-flow will increase the danger of failure) and the presence of firm divisions (branches). In such circumstances, extra servers could also be required to put in the SIEM system, because it’s preferable to distribute collector and correlator providers throughout completely different servers for such excessive EPS flows.
Information movement: 200 000 EPS
As EPS flows develop and the infrastructure divides into separate unbiased models, the quantity of kit required will increase accordingly. Further servers can be wanted for collectors, storage, correlators, and keepers. Furthermore, in giant organizations, information availability necessities might take priority. On this case, the Kaspersky Unified Monitoring and Evaluation Platform storage cluster divides all collected occasions into shards. Every shard consists of a number of information replicas. And every shard duplicate is a cluster node, that means a separate server. To make sure resilience and efficiency, we suggest deploying the cluster with two replicas per shard. For processing such giant EPS volumes, three collector servers could also be required, put in within the workplaces with the best occasion flows.
Kaspersky SIEM in holding corporations
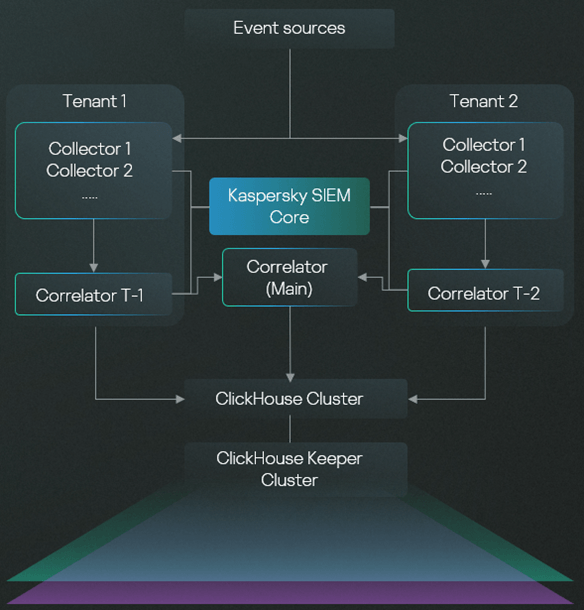
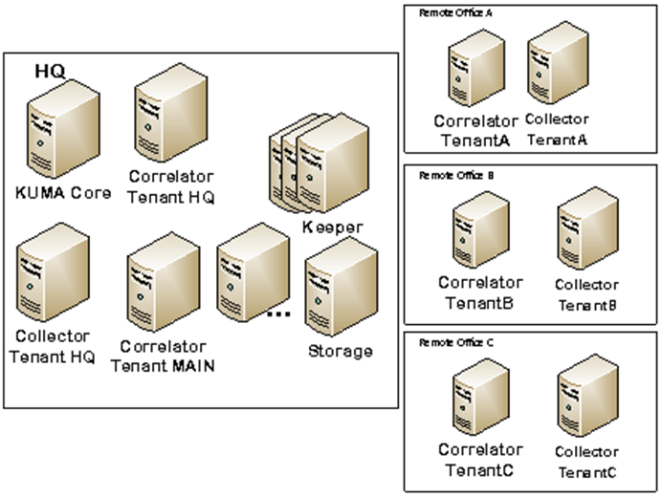
In giant enterprises, the price of implementing an SIEM system will increase not solely with the quantity of information, but additionally relying on the utilization profile. For instance, in some circumstances (equivalent to MSP and MSSP environments, in addition to giant holding corporations with a number of subsidiaries or branches), multi-tenancy is required. This implies the corporate wants to take care of a number of “mini-SIEMs”, which function independently. Our answer allows this via a single set up on the head workplace, with out the necessity to set up separate methods in/at every department/tenant. This considerably reduces tools prices.
Let’s think about both (i) a holding firm, (ii) a vertically-integrated enterprise, or (iii) a geographically-distributed company with both numerous unbiased safety groups or a have to isolate information entry amongst branches. The Kaspersky Unified Monitoring and Evaluation Platform tenant mannequin permits for segregated entry to all sources, occasions, and third-party integration settings. This implies one set up capabilities as a number of separate SIEM methods. On this case, whereas every tenant can develop its personal content material (correlation guidelines), there’s additionally the choice of distributing a unified set of sources throughout all divisions. In different phrases, every division can have its personal collectors, correlators, and guidelines, however the HQ safety workforce also can assign standardized bundles of safety content material for everybody — guaranteeing constant safety throughout the group.
Thus, utilizing the Kaspersky Unified Monitoring and Evaluation Platform ensures the mandatory efficiency with comparatively modest computing sources. In some circumstances, financial savings on {hardware} can attain as much as 50%.
For a extra correct understanding of the required sources and implementation prices, we suggest speaking with our specialists or integration companions. We (or our companions) also can present premium help, help in growing further integrations (together with utilizing API capabilities for related merchandise), and oversee the deployment of a turnkey answer overlaying system design, tools estimation, configuration optimization, and rather more. Be taught extra about our SIEM system, the Kaspersky Unified Monitoring and Evaluation Platform, on the official product web page.