Pharming definition: Pharming is a cyberattack that redirects customers from reliable web sites to pretend ones, typically with out their information.
Image this: You enter your financial institution’s URL, however as an alternative of the true website, you’re unknowingly directed to a counterfeit one. That is pharming — an alarming cyberattack that tips customers into handing over delicate data like passwords or monetary particulars. For residence customers, the risks of pharming are actual, and it might probably occur with out you even figuring out.
Pharming is particularly dangerous as a result of it doesn’t depend on person actions like clicking suspicious hyperlinks. As an alternative, cybercriminals use malicious code to redirect you to pretend web sites routinely. Be taught extra about this assault and how one can forestall it.
What Is Pharming?
In pharming scams, hackers manipulate web site visitors, redirecting customers to pretend web sites with out their information. In contrast to conventional phishing assaults, which depend on tricking customers into clicking suspicious hyperlinks, pharming operates within the background. Hackers set up malicious code on a sufferer’s pc or server, altering the system’s IP handle settings. Consequently, even when you kind within the appropriate URL, you’re redirected to a pretend web site designed to steal delicate data.
What makes pharming notably harmful is its capability to focus on a number of customers without delay. Since hackers can plant malicious code on a big scale — via compromised servers or contaminated units — they will execute these assaults with out instantly interacting with you.
When you land on these pretend web sites, it’s possible you’ll unknowingly enter private information, equivalent to passwords or bank card particulars, which cybercriminals use for identification theft or monetary fraud.
How Does Pharming Work?
Pharming assaults can happen in two major methods: via DNS-based pharming or host-based pharming. Each strategies depend on manipulating the best way your gadget connects to web sites, redirecting you to fraudulent websites.
Right here’s how DNS assaults work:
- DNS cache poisoning: Hackers corrupt the DNS cache with false data, rerouting you to malicious web sites with out altering the unique URL.
- Rogue DNS servers: Cybercriminals arrange rogue DNS servers that routinely redirect net visitors to pretend websites, making it troublesome to detect the rip-off.
- DNS server compromise: Hackers infiltrate reliable DNS servers, altering their information to mislead giant numbers of customers into visiting counterfeit web sites.
- DNS hijacking: Attackers take over DNS settings on a sufferer’s gadget or router, redirecting visitors to phishing websites with out the person’s information.
- Credential pharming: This tactic goals to seize login credentials by directing customers to pretend login pages, typically bypassing safety measures like CAPTCHA verification.
Host-based pharming can occur via:
- Host file modifications: Malicious software program modifies a tool’s native host file, forcing it to redirect to fraudulent web sites even when the person enters reliable URLs.
- Malware an infection: Malware infects a tool, permitting hackers to govern DNS settings or browser configurations to redirect customers to phishing websites.
- Router DNS configuration manipulation: Attackers exploit vulnerabilities in a person’s router, altering DNS configurations to reroute all related units to phishing web sites.
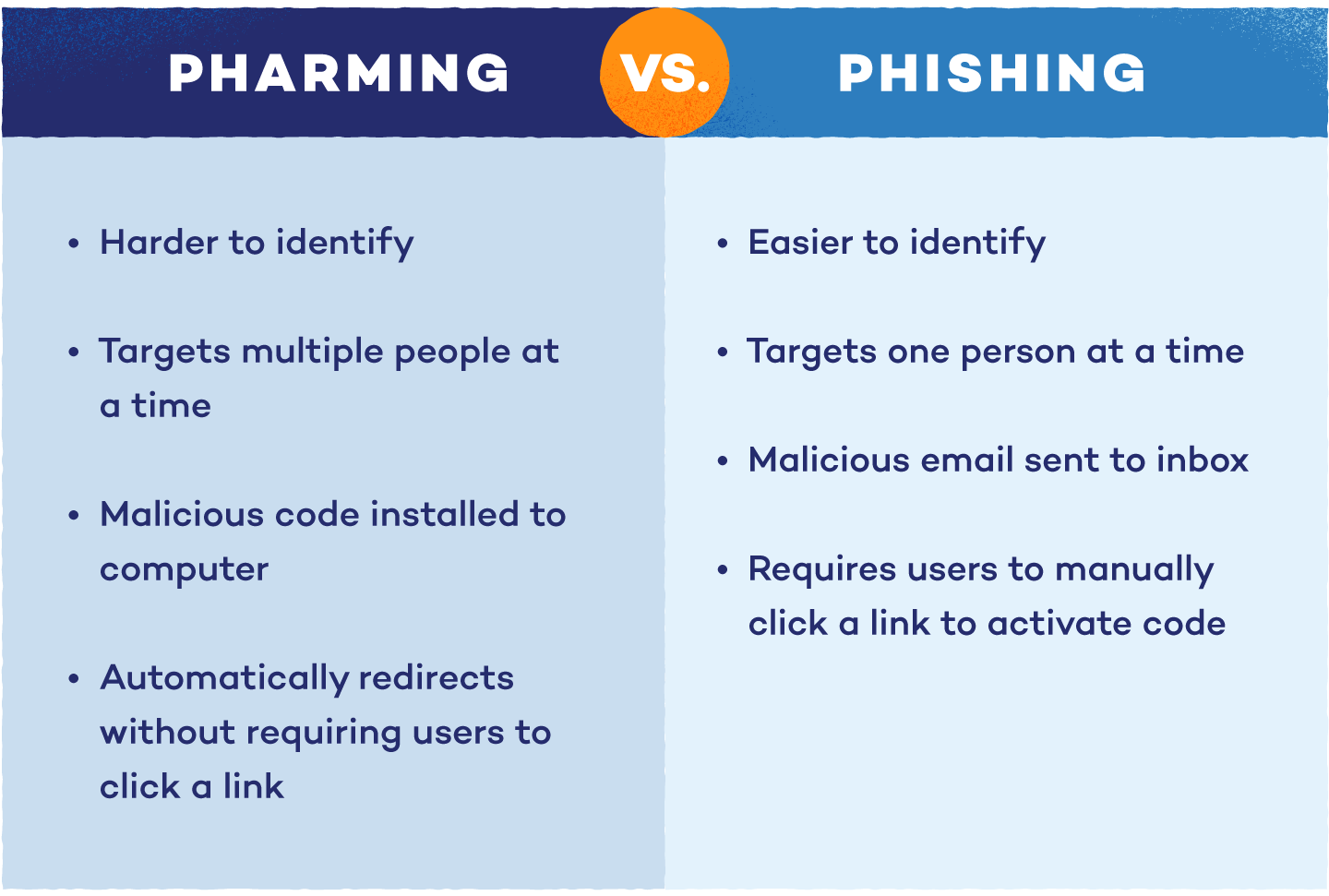
Pharming vs. Phishing
With so many “ph-” phrases in cybersecurity, it may be tough to differentiate between pharming, phishing and different assaults. Whereas each purpose to steal private data, the strategies are totally different.
Phishing assaults trick customers into sharing delicate data by sending pretend emails that seem reliable. These emails typically embrace hyperlinks that result in fraudulent web sites or attachments that set up malware. Phishing isn’t restricted to electronic mail — it might probably additionally occur via textual content messages (smishing) or voice messages (vishing). To forestall phishing assaults, you’ll want to be cautious of unsolicited messages and confirm the sender’s legitimacy.
Pharming, alternatively, is extra covert. It redirects you to counterfeit web sites with none motion required, typically via malware or DNS manipulation. In contrast to phishing, the place a person should click on on a malicious hyperlink, pharming works within the background, making it more durable to detect.
Pharming Examples
Pharming assaults might not at all times make headlines, however they will have devastating results on people and organizations alike. These assaults typically goal monetary establishments and different delicate providers, silently redirecting customers to fraudulent web sites. Listed here are a few examples that illustrate the risks of pharming:
- Brazilian financial institution assault (2017): Cybercriminals efficiently redirected all visitors from a serious Brazilian financial institution’s web site to a pretend model hosted on malicious servers. Over a number of hours, attackers captured login credentials from numerous clients, resulting in vital monetary losses.
- DNSChanger malware (2007): The DNSChanger malware contaminated thousands and thousands of computer systems globally. It altered DNS settings and redirected customers to fraudulent web sites and commercials, serving to them generate thousands and thousands in advert income.
Indicators of Pharming
Pharming could be tough to detect, however staying alert to sure crimson flags can assist you notice potential assaults. Listed here are some frequent indicators to observe for:
- Delicate modifications to a hyperlink or web site: If the URL appears barely totally different or the web site format appears off, you’ll have been redirected to a pretend website.
- Unsafe connection: A lacking padlock icon or “not safe” warning within the browser might point out you’re on a fraudulent website. All the time examine for a safe connection earlier than coming into any private data.
- Uncommon account or banking exercise: Unexplained transactions or login makes an attempt may end up from a pharming assault. Monitoring your accounts intently can assist catch these early.
- Unauthorized password modifications: When you’re locked out of your accounts or discover a password change you didn’t provoke, it may very well be an indication that hackers have gained entry.
- Unfamiliar apps or downloads: Sudden software program or downloads in your gadget might point out a malware an infection linked to pharming. Common malware removing checks can forestall additional injury.
- Pop-ups asking for private data: Reputable websites not often request private particulars through pop-ups, so deal with these with warning.
- Emails and texts containing suspicious hyperlinks: Even when the message appears official, hyperlinks might result in pretend web sites designed to steal your data. All the time confirm earlier than clicking.
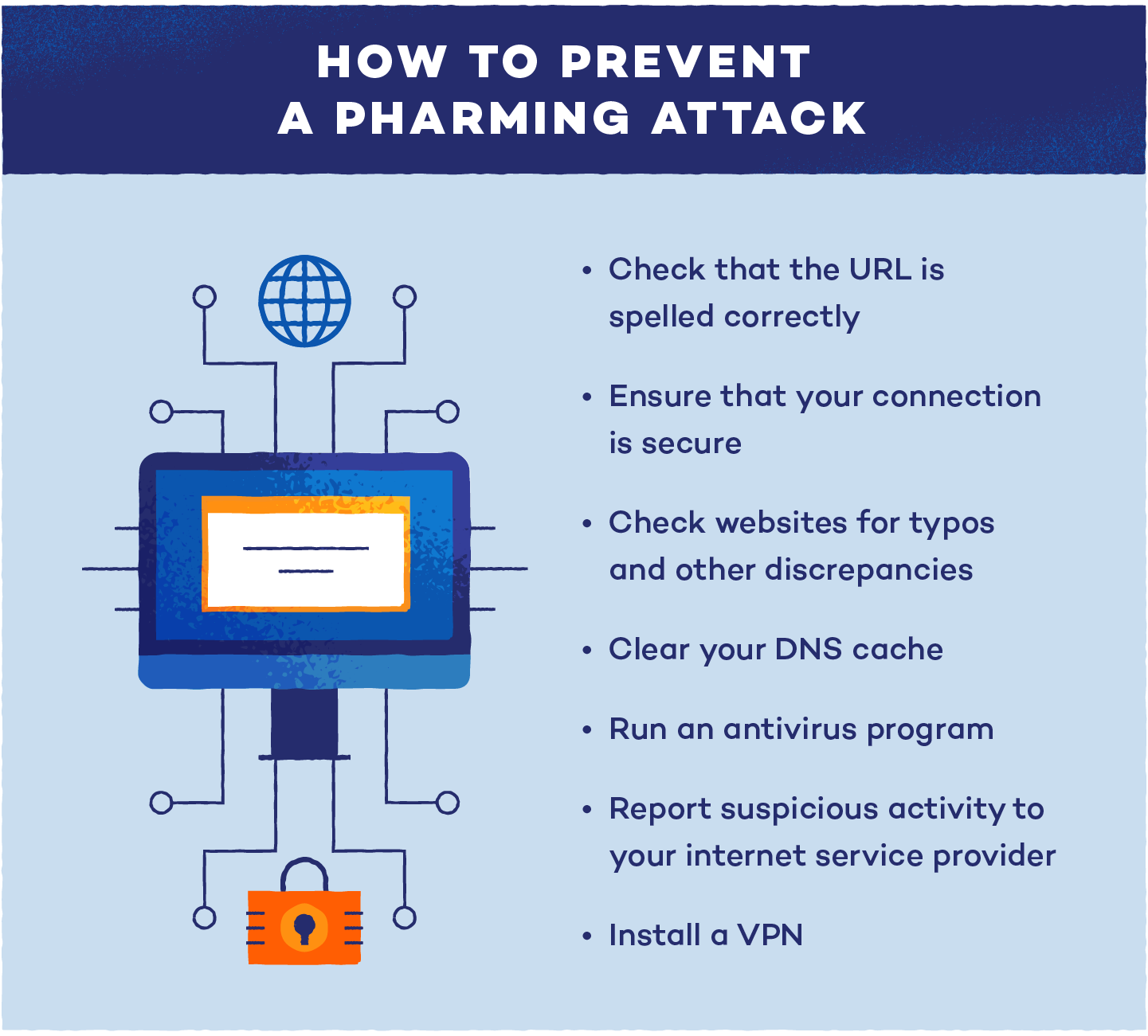
The best way to Forestall Pharming Assaults
Listed here are some helpful tricks to forestall pharming:
- Clear your DNS cache recurrently: When you suspect a pharming assault, clearing your DNS cache can take away any corrupted entries which may redirect you to fraudulent websites.
- Run antivirus and malware removing software program: Protecting your antivirus program up-to-date is essential for detecting and eradicating malicious code. Common scans assist guarantee your gadget stays protected against hidden threats.
- Use a VPN: A digital non-public community (VPN) encrypts your web visitors, making it more durable for cybercriminals to intercept your information or redirect you to pretend web sites.
- Allow multi-factor authentication (MFA): MFA provides an additional layer of safety to your accounts, requiring a number of types of verification. This can assist forestall hackers from accessing delicate data even when they receive your credentials.
- Replace your software program and firmware: Frequently updating your gadget’s working system, router firmware and browser helps patch vulnerabilities that may very well be exploited in a pharming assault.
- Monitor your accounts: Keep watch over your monetary and on-line accounts for any uncommon exercise, and report something suspicious instantly.
- Use safe HTTPS web sites: Make sure the web sites you go to use HTTPS, which encrypts your information. That is indicated by a padlock icon within the browser’s handle bar, offering an additional degree of safety.
- Contact your web service supplier (ISP): When you suspect that your DNS settings or server has been compromised, contact your ISP instantly for help resolving the difficulty.
Begin Searching With Confidence
Pharming assaults can have critical penalties, from stolen private data to drained financial institution accounts. With hackers continuously refining their strategies, it’s essential to remain forward of threats by being conscious of the risks and taking steps to guard your on-line exercise. The excellent news? You don’t need to navigate these dangers alone.
With Panda Safety, you get cutting-edge instruments to safeguard your searching. From real-time malware safety to safe VPN entry, Panda helps you block threats earlier than they attain you. Whether or not stopping pharming makes an attempt or stopping phishing assaults, Panda Safety has the options to maintain your information and units secure.



