The need to stay nameless on-line is as previous because the web itself. Prior to now, customers believed hiding behind a nickname meant they may badmouth their neighbors on native boards with impunity. Now, such trolls may be recognized in seconds. Since these early days, know-how has taken a quantum leap: distributed networks, nameless browsers, and different privateness instruments have emerged. One among these instruments, which was closely promoted a decade in the past by former NSA contractor Edward Snowden, is the Tor Browser, the place “TOR” is an acronym for “The Onion Router”.
However in at present’s world, can Tor actually present full anonymity? And if it doesn’t, ought to we simply overlook all about anonymity and depend on a daily browser like Google Chrome?
How Tor customers are deanonymized
If Tor is new to you, try our classic article from method again when. There, we answered some frequent questions: how the browser ensures anonymity, who wants it, and what individuals often do on the darkish internet. Briefly, Tor anonymizes consumer site visitors by way of a distributed community of servers, referred to as nodes. All community site visitors is repeatedly encrypted because it passes by way of a lot of nodes between two speaking computer systems. No single node is aware of each the origin and vacation spot addresses of an information packet, nor can it entry the packet’s content material. OK, brief digression over — now let’s flip to the actual safety threats going through anonymity lovers.
In September, German intelligence providers recognized a Tor consumer. How did they do it? The important thing to their success was information obtained by way of what’s referred to as “timing evaluation”.
How does this evaluation work? Regulation enforcement companies monitor Tor exit nodes (the ultimate nodes within the chains that ship site visitors to its vacation spot). The extra Tor nodes the authorities monitor, the better the possibility a consumer hiding their connection will use a type of monitored nodes. Then, by timing particular person information packets and correlating this info with ISP information, legislation enforcement can hint nameless connections again to the top Tor consumer — despite the fact that all Tor site visitors is encrypted a number of occasions.
The operation described above, which led to the arrest of the administrator of a kid sexual abuse platform, was doable partly as a result of Germany hosts the highest variety of Tor exit nodes — round 700. The Netherlands ranks second with about 400, and the US is available in third with round 350. Different nations have anyplace from a couple of to some dozen. Worldwide cooperation amongst these high exit-node nations performed a big position in deanonymizing the kid sexual abuse offender. Logically, the extra nodes a rustic has, the extra of them may be state-monitored, rising the chance of catching criminals.
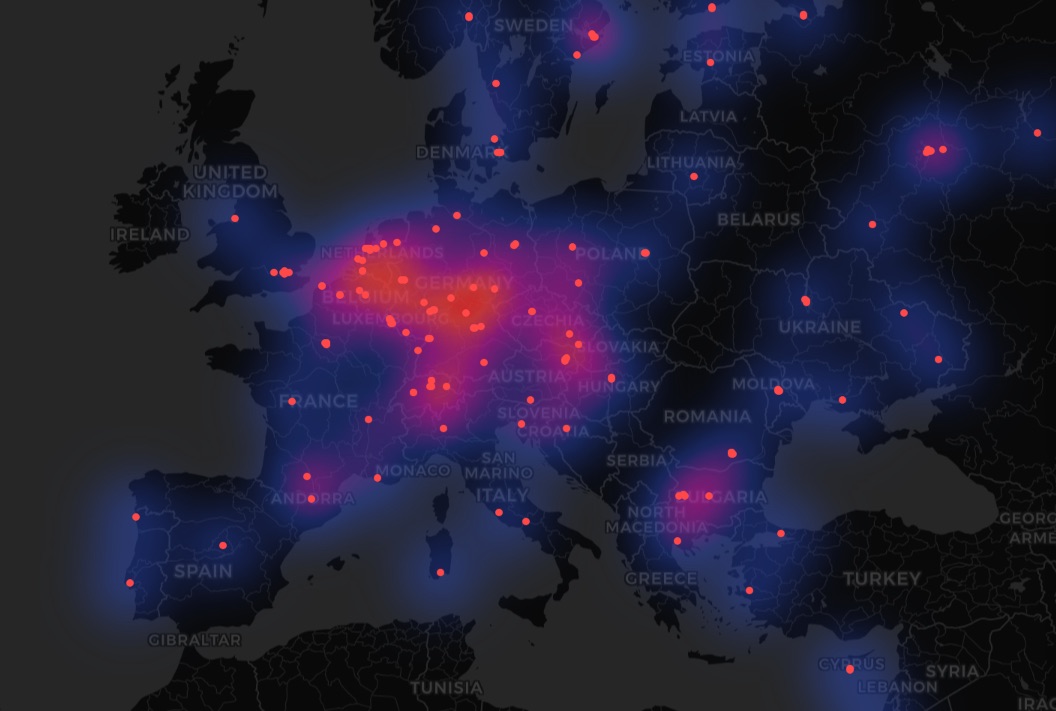
Germany and the Netherlands are among the many leaders on the variety of Tor exit nodes — not solely in Europe however worldwide. Supply
The Tor Challenge responded with a weblog publish discussing the protection of their browser. It concludes that it’s nonetheless protected: the de-anonymized particular person was a legal (why else would authorities have an interest?), utilizing an outdated model of Tor and the Ricochet messaging app. Nonetheless, Tor famous it wasn’t given entry to the case recordsdata, so their interpretation relating to the safety of their very own browser may not be definitive.
This type of story isn’t new; the issue of timing assaults has lengthy been recognized to the Tor Challenge, intelligence companies, and researchers. So though the assault technique is well-known, it stays doable, and most definitely, extra criminals will likely be recognized by way of timing evaluation sooner or later. Nonetheless, this technique isn’t the one one: in 2015, our consultants carried out in depth analysis detailing different methods to assault Tor customers. Even when a few of these strategies have change into outdated within the varieties offered in that research, the rules of those assaults stay unchanged.
“Usually it’s inconceivable to have excellent anonymity, even with Tor”.
This phrase opens the “Am I completely nameless if I take advantage of Tor?” part of the Tor Browser help web page. Right here, the builders present ideas, however the following pointers can at finest solely improve the possibilities of remaining nameless:
- Management what info you present by way of internet varieties. Customers are suggested in opposition to logging in to non-public accounts on social networks, in addition to posting their actual names, e-mail addresses, telephone numbers, and different related info on boards.
- Don’t torrent over Tor. Torrent packages usually bypass proxy settings and like direct connections, which may de-anonymize all site visitors — together with Tor.
- Don’t allow or set up browser plugins. This recommendation additionally applies to common browsers, as there are numerous harmful extensions on the market.
- Use HTTPS variations of internet sites. This suggestion, by the way, applies to all web customers.
- Don’t open paperwork downloaded by way of Tor whereas on-line. Such paperwork, the Tor Challenge warns, could comprise malicious exploits.
With all these suggestions, the Tor Challenge is actually issuing a disclaimer: “Our browser is nameless, however if you happen to misuse it, you should still be uncovered”. And this truly is sensible — your degree of anonymity on-line relies upon primarily in your actions as a consumer — not solely on the technical capabilities of the browser or another software.
There may be one other fascinating part on the Tor help web page: “What assaults stay in opposition to onion routing?” It particularly mentions doable assaults utilizing timing evaluation with the word that “Tor doesn’t defend in opposition to such a risk mannequin”. Nonetheless, in a publish concerning the German consumer’s de-anonymization, the builders declare that an add-on referred to as Vanguard, designed to guard in opposition to timing assaults, has been included in Tor Browser since 2018, and in Ricochet-Refresh since June 2022. This discrepancy suggests one among two issues: both the Tor Challenge hasn’t up to date its documentation, or it’s being considerably disingenuous. Each are problematic as a result of they will mislead customers.
So what about anonymity?
It’s vital to do not forget that Tor Browser can’t assure 100% anonymity. On the similar time, switching to different instruments constructed on an analogous distributed node community construction is pointless, as they’re equally weak to timing assaults.
When you’re a law-abiding particular person utilizing nameless shopping merely to keep away from intrusive contextual advertisements, secretly store for presents for family members, and for different equally innocent functions, the personal shopping mode in any common browser will in all probability suffice. This mode, in fact, doesn’t provide the identical degree of anonymity as Tor and its counterparts, however it might make browsing the online a bit extra… effectively, personal. Simply be sure you absolutely perceive how this mode works in numerous browsers, and what it might and might’t shield you from.
As well as, all of our house safety options embody Personal Searching. By default, this characteristic detects makes an attempt to gather information and logs them in a report however doesn’t block them. To dam information assortment, it’s essential both allow Block information assortment within the Kaspersky app or activate the Kaspersky Safety plugin instantly within the browser.
In addition to this, our safety can even block advertisements, forestall the hidden set up of undesirable apps, detect and take away stalkerware and adware, and take away traces of your exercise within the working system. In the meantime, the particular part Secure Cash gives most safety for all monetary operations by conducting them in a protected browser in an remoted surroundings and stopping different apps from gaining unauthorized entry to the clipboard or taking screenshots.
Double VPN
You can even keep nameless on the web utilizing Kaspersky VPN Safe Connection that help Double VPN (often known as multi-hop). Because the title suggests, this know-how lets you create a sequence of two VPN servers in numerous components of the world: your site visitors first passes by way of an middleman server, after which by way of one other. Double VPN in Kaspersky VPN Safe Connection makes use of nested encryption — the encrypted tunnel between the shopper and the vacation spot server runs inside a second encrypted tunnel between the shopper and the middleman server. Encryption in each circumstances is barely carried out on the shopper aspect, and information isn’t decrypted on the middleman server. This gives a further layer of safety and anonymity.
Double VPN is obtainable to customers of Home windows and Mac variations of Kaspersky VPN Safe Connection. Earlier than enabling Double VPN, ensure that the Catapult Hydra protocol is chosen within the software settings: Primary → Settings (gear icon) → Protocol → Choose robotically, or Catapult Hydra.
After that, you’ll be able to allow Double VPN:
- Open the principle software window.
- Click on the Location drop-down to open the listing of places of VPN servers.
- Click on the Double VPN
- Choose two places and click on Join.
You may add your Double VPN server pair to Favorites by clicking the Add to Favorites button.
Congratulations! Now your site visitors is encrypted extra securely than ordinary — however do not forget that these site visitors encryption strategies will not be supposed for unlawful actions. Double VPN will allow you to conceal private info from data-gathering websites, keep away from undesirable advertisements, and entry sources unavailable in your present location.