Steam the Webinar on demand HERE
As we glance again on the cybersecurity panorama of 2024, it’s clear that the world of digital threats continues to evolve at an alarming tempo in parallel with AI. This yr has seen ransomware teams adapt and innovate, pushing the boundaries of their malicious capabilities and evasiveness from regulation enforcement. In our annual “Nastiest Malware” report, now in its sixth yr, we’ve noticed a gradual enhance in each the quantity and class of malware assaults. The ransomware sector, particularly, has witnessed the emergence of “enterprise fashions,” with ransomware-as-a-service (RaaS) dominating the scene. Elite ransomware authors have concluded that revenue sharing and threat mitigation are key contributors to their constant success and evasion of authorities.
The saga of LockBit in 2024 exemplifies the resilience and flexibility of those cybercriminal teams. Regardless of a significant regulation enforcement operation in February, dubbed “Operation Cronos,” which noticed the FBI and worldwide companions seize LockBit’s infrastructure and procure over 7,000 decryption keys, the group managed to resurface inside days. This cat-and-mouse recreation between LockBit and regulation enforcement companies has continued all year long, with the group’s chief even taunting the FBI, claiming that their efforts solely make LockBit stronger. The LockBit story underscores a vital level: whereas regulation enforcement operations can disrupt cybercriminal actions, they usually fall wanting delivering a knockout blow. These teams have develop into adept at rebuilding their infrastructure, rebranding when crucial, and persevering with their operations with minimal downtime.
As we element our evaluation of the six most infamous ransomware and malware teams which have dominated headlines in 2024, it’s vital to notice that the menace panorama extends past simply these actors. The rise of AI-driven phishing and social engineering, elevated focusing on of vital infrastructure, and the emergence of extra subtle fileless malware are all tendencies which have formed the cybersecurity battlefield this yr.
On this report, we’ll discover how these teams have advanced, their most vital assaults, and the broader implications for cybersecurity. We’ll additionally present up to date survival ideas for each companies and particular person customers, reflecting the ever-changing nature of those threats.
Ransomware
Over the previous decade, ransomware has established itself as the top of cybercriminal exploits. It’s essentially the most profitable and profitable avenue for monetizing a breach of a sufferer. Yearly we see increasingly more knowledge stolen and better ransom calls for dominating headlines. Every ransomware group on our Nastiest Malware listing makes use of the double-extortion methodology the place the info stolen is leveraged for leak potential on darkish net leak websites. The approaching injury to model and popularity that comes with the general public disclosure of a breach are large threats to firms of any dimension. To not point out the upcoming regulatory fines that include the breach. This technique has proven it’s resilience over the previous few years because it turned mainstream and it appears to be as strong as ever. Let’s check out what the fee numbers appear like thus far in 2024.
Supply: Coveware
We’ve seen a drop-off from the highs final yr – fueled by Cl0p ransomware group making over $100 Million in just a few months in late 2023. However once we zoom out you possibly can see that will probably be going up over time. This time subsequent yr we anticipate the quantities to be larger than what they’re now. A few of this might be fueled by inflation, some might be a rise in effectiveness in techniques, and a few by the anticipated 2025 “bull run” value spike in crypto – the one fee methodology these criminals settle for.
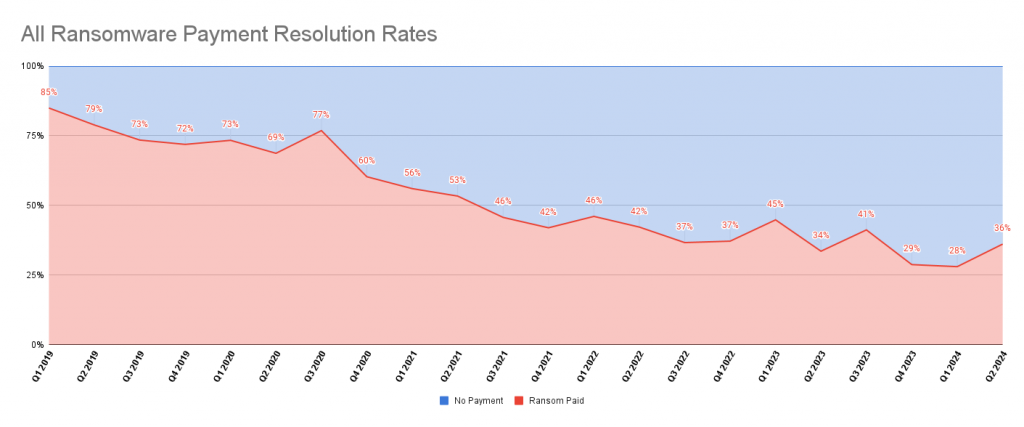
Wanting on the fee decision charges – which means the proportion of those who find yourself paying the ransom, we will see a slight enhance throughout this yr. Zooming out the development does point out an general decline which is nice information and displays that the business is taking critical precautions of their safety posture. We count on that this slight enhance is barely non permanent and can proceed the development of lowering for subsequent yr.
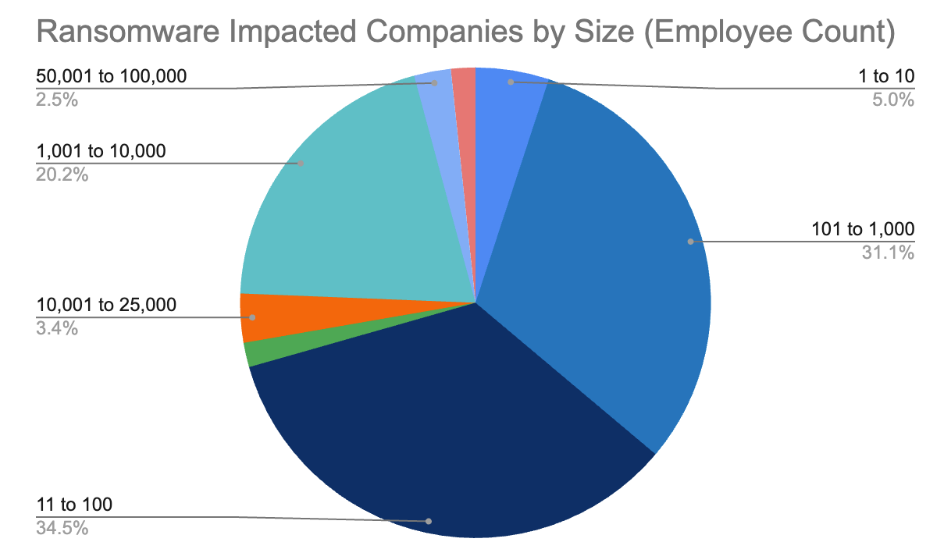
One nasty change this yr is the rise of ransomware assaults on smaller sized companies. The market share of ransomware assaults on enterprise with beneath 100 workers is now nearly 40%. Whereas the media headlines of file breaking ransoms towards fortune 500 firms will at all times take heart stage, the small to mid market has at all times been the bread and butter for cybercriminals. The quantity of effort and return on funding of time is simply too good for criminals to not be attracted to those simpler and weaker targets. Now let’s check out this yr’s Nastiest Malware.
LockBit: The Resilient Risk

Probably the most infamous ransomware teams, LockBit, confronted vital challenges and disruptions in 2024 because of coordinated worldwide regulation enforcement efforts. The yr started with “Operation Cronos,” a significant strike towards LockBit’s infrastructure in February. Led by the UK’s Nationwide Crime Company (NCA) and involving companies from a number of international locations, together with the FBI, this operation resulted within the seizure of LockBit’s leak websites and the publicity of details about almost 200 associates. A pivotal second got here when the FBI obtained over 7,000 decryption keys, permitting victims to unlock their encrypted knowledge without cost. This dealt a extreme blow to LockBit’s operations and credibility – do not forget that many of the success and cash is from the associates that select thier ransomware payload over one other’s group so credibility and belief are paramount on this criminals scene.
Regardless of these setbacks, LockBit tried to keep up its operations, rapidly adapting by altering encryption strategies and shifting its leak website technique. Nevertheless, regulation enforcement continued to use strain all year long. In Might, authorities revealed the id of LockBit’s alleged mastermind, Dmitry Yuryevich Khoroshev, and supplied a $10 Million reward for info resulting in his arrest. The end result of those efforts got here in October when regulation enforcement companies introduced extra arrests and disruptions. 4 people linked to LockBit had been arrested, together with a significant developer and two associates. Notably, Aleksandr Ryzhenkov, linked to each LockBit and the notorious Evil Corp group, was unmasked and sanctioned. These actions, a part of the continued Operation Cronos, considerably impacted LockBit’s operations, resulting in a noticeable lower of their assault frequency and inflicting mistrust throughout the cybercriminal group.
Regardless of LockBit’s makes an attempt to keep up its fearsome popularity, together with false claims of assaults, the group’s actions had been impacted all through 2024, marking a big victory for world cybersecurity efforts. Nevertheless, LockBit continues to be a significant participant within the RaaS scene and the chief and his associates are nonetheless making tens of millions in ransoms. LockBit has confirmed its resilience within the face of regulation enforcement efforts, presenting the group’s adaptability and persistence. The chief has boasted that he loves the FBI and that they solely make his group stronger, and he desires to hit a million companies earlier than retirement. It is a stark distinction from most ransomware teams when hit by regulation enforcement as they’ll rapidly retire the model and repivot to a different. This RaaS has been on the Nastiest Malware for over three years sustaining its standing as a prime contender within the Ransomware scene in 2024.
Akira: The Healthcare Menace
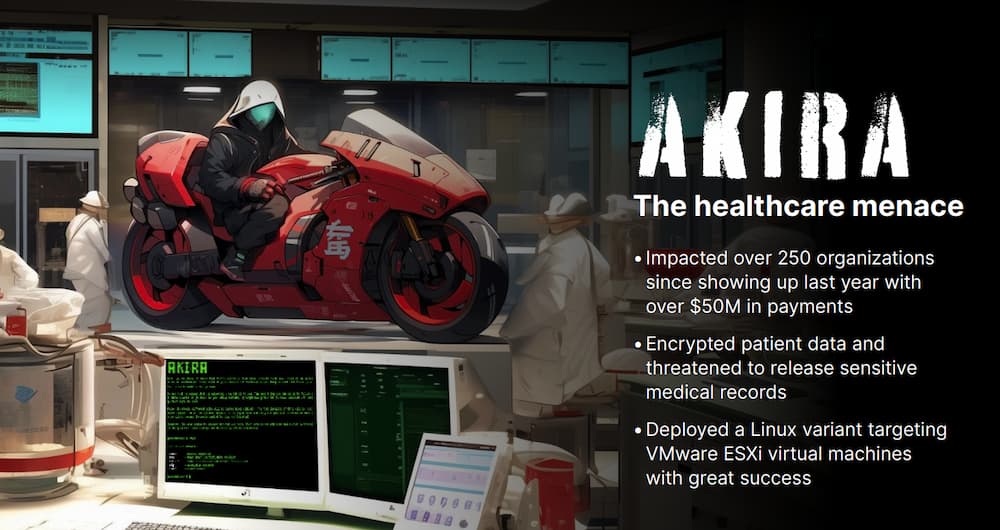
The Akira ransomware group was first noticed in March 2023 and instantly turned probably the most formidable threats within the menace panorama. By January 2024, the group had impacted over 250 organizations and claimed roughly $42 million in ransomware proceeds. Akira’s fast rise to the highest was marked by its versatility and fixed evolution of techniques. In 2024, Akira expanded its capabilities considerably. Initially targeted on Home windows methods, the group deployed a Linux variant focusing on VMware ESXi digital machines in April. All year long, Akira demonstrated a sample of swift adaptation to new vulnerabilities. They actively exploited a number of vital vulnerabilities, together with SonicWall SonicOS, Cisco Adaptive Safety Equipment (ASA), and FortiClientEMS software program. These exploits allowed Akira to achieve preliminary entry, escalate privileges, and transfer laterally inside compromised networks.
A notable shift in Akira’s techniques occurred in early 2024 after they appeared to sideline encryption techniques, focusing totally on knowledge exfiltration. Nevertheless, by September 2024, there have been indications of a possible return to earlier techniques utilizing Home windows and Linux payloads written in C++. This adaptability was additional evidenced in a June 2024 assault on a Latin American airline, the place Akira operators exploited susceptible companies to deploy ransomware and exfiltrate knowledge.
Akira’s victims spanned a variety of sectors, with a specific deal with manufacturing, skilled companies, healthcare, and demanding infrastructure. The group’s success was attributed to its fixed evolution, subtle assault strategies, and the employment of double-extortion techniques. As of 2024, Akira had solidified its place as probably the most prevalent and harmful ransomware operations within the cybersecurity menace panorama.
RansomHub: The Excessive-Profile Attacker

RansomHub emerged as a formidable new participant within the ransomware panorama in February 2024, rapidly establishing itself as probably the most prolific and harmful ransomware teams. Working on a RaaS mannequin, RansomHub attracted high-profile associates from different distinguished teams like BlackCat/ALPHV following their FBI takedown in December 2023. That is possible because of its engaging fee construction the place associates obtain as much as 90% of the ransom – in comparison with round 30-50% with different teams.
By August 2024, RansomHub had breached no less than 210 victims throughout varied vital U.S. infrastructure sectors, together with healthcare, authorities companies, monetary companies, and demanding manufacturing. Notable assaults included breaches of Deliberate Parenthood, the Ceremony Help drugstore chain, Christie’s public sale home, and Frontier Communications, with the latter ensuing within the publicity of private info of over 750,000 prospects. RansomHub’s techniques advanced all year long, using subtle strategies akin to exploiting varied software program vulnerabilities, utilizing intermittent encryption to hurry up assaults, and leveraging double extortion methods. The group’s knowledge leak website turned a big menace, with stolen knowledge being printed for 3-90 days if ransom calls for weren’t met.
The assault on Deliberate Parenthood not solely demonstrated RansomHub’s functionality to breach extremely delicate networks but additionally highlighted their willingness to focus on organizations with excessive reputational dangers. This sparked widespread concern and discussions on cybersecurity measures inside nonprofit organizations. By October 2024, RansomHub had overtaken LockBit as essentially the most prolific ransomware group by way of claimed profitable assaults, solidifying its place as a significant menace within the cybersecurity panorama.
Darkish Angels: The Whaling Specialists

Darkish Angels emerged as probably the most formidable ransomware threats in 2024, gaining notoriety for his or her extremely focused “large recreation searching” method and record-breaking ransom calls for. The group, which has been lively since 2022, made headlines in early 2024 after they reportedly acquired a staggering $75 million ransom fee from a Fortune 50 firm. This fee can be almost double the earlier file of $40 million paid by CNA Monetary in 2021.The group’s modus operandi includes focusing on a small variety of high-value organizations, usually exfiltrating large quantities of information (sometimes 10-100 terabytes for giant companies) earlier than contemplating encryption. This technique permits Darkish Angels to keep up a low profile whereas maximizing their earnings.
In 2024, they continued to evolve their techniques, switching from a Babuk-ESXi-based ransomware to a variant of Ragnar Locker. Notable assaults attributed to Darkish Angels in 2024 included a breach of a high-profile media firm, the place they stole proprietary info and engaged in prolonged negotiations earlier than the ransom was paid. The group’s knowledge leak website, named “Dunghill Leak,” is used to strain victims into paying, although the group usually prefers to keep away from public consideration. Darkish Angels’ success in 2024, notably the record-breaking ransom fee, has raised considerations that their techniques could also be emulated by different cybercriminal teams, probably resulting in a rise in extremely focused, high-value ransomware assaults throughout varied sectors.
RedLine: The Credential Thief

Not all of our Nastiest Malware are ransomware teams and RedLine Stealer has develop into probably the most distinguished threats in 2024, notably because of its functionality to steal credentials and delicate knowledge throughout a wide selection of sectors. All through 2024, RedLine demonstrated its effectiveness by stealing over 170 million passwords in only a six-month interval, highlighting its large affect. The malware’s capabilities expanded to incorporate stealing not solely passwords but additionally bank card particulars, cryptocurrency wallets, and browser knowledge. Its adaptability and frequent updates allowed it to evade many safety measures, making it a persistent menace throughout varied sectors.
RedLine’s distribution strategies remained numerous, with phishing emails and malicious web sites being the first vectors. The malware’s operators continued to refine their techniques, usually disguising RedLine as respectable software program updates or engaging downloads. This method allowed them to bypass conventional safety measures and infect numerous methods. The affect of RedLine prolonged past particular person customers to have an effect on main firms and demanding infrastructure. A number of high-profile breaches attributed to RedLine in 2024 resulted in vital monetary losses and reputational injury for the affected organizations.
Breaking information!
In late October 2024 – RedLine suffered a takedown from a coordinated worldwide regulation enforcement operation dubbed “Operation Magnus.” Led by the Dutch Nationwide Police and supported by companies together with the FBI, UK’s Nationwide Crime Company, the operation efficiently disrupted RedLine’s infrastructure and operations. The authorities gained full entry to RedLine’s servers, acquiring essential knowledge together with usernames, passwords, IP addresses, and even the supply code of the malware. This breakthrough allowed regulation enforcement to retrieve a database of 1000’s of RedLine shoppers, paving the best way for additional investigations and potential authorized actions towards cybercriminals who used the malware. The U.S. Division of Justice charged Maxim Rudometov, a Russian nationwide, because the suspected developer and chief of the RedLine malware operation. If convicted, Rudometov faces as much as 35 years in jail on fees together with entry gadget fraud, conspiracy to commit laptop intrusion, and cash laundering.
Solely time will inform if this seizure of belongings is sufficient to shutdown the operations of RedLine and stop them from bouncing again like we’ve seen time and time once more from different resilient teams on this listing.
Play Ransomware: The Versatile Risk

Play ransomware continued to be a big menace within the cybersecurity panorama all through 2024. The group, which first appeared in 2022, maintained its place as probably the most lively ransomware operations, constantly rating among the many prime menace actors. In 2024 a notable shift occurred when the group transitioned from its earlier double-extortion techniques to particularly focusing on ESXi environments. This variation in focus allowed Play to use vulnerabilities in digital machine infrastructures, rising the affect of their assaults.
A major assault attributed to Play Ransomware focused a significant utility supplier, leading to widespread service disruptions and elevating considerations about vital infrastructure vulnerabilities. The assault started with the exploitation of unpatched FortiOS vulnerabilities within the firm’s VPN infrastructure, permitting preliminary entry to the community. From there, the attackers leveraged uncovered RDP companies to maneuver laterally throughout the community, ultimately gaining the entry wanted to deploy their ransomware payload.
The group’s use of intermittent encryption continued to be a defining attribute, permitting them to evade many endpoint safety options whereas nonetheless rendering information inaccessible to victims. Play’s assaults had been notably damaging within the IT companies sector, suggesting a strategic deal with organizations that would result in provide chain impacts.

AI-Pushed Phishing and Social Engineering:
- Using AI and machine studying in crafting phishing emails has made these lures extra convincing and tougher to detect. Cybercriminals are leveraging AI to personalize assaults, rising their success charges
Focusing on of Vital Infrastructure:
- There was a noticeable enhance in assaults focusing on vital infrastructure, together with utilities and healthcare sectors, elevating considerations about nationwide safety and public security
Fileless Malware:
- Fileless assaults aren’t new, and neither is bypassing safety protections however there was a rise in tougher to detect kill chains, extra subtle assaults, extra complicated persistence, which might be more practical at bypassing safety than ever.
New Malware Language:
- Malware written in Golang continues to development in each scale and complexity

Companies:
- Lock down Distant Desktop Protocols (RDP) – this infiltration tactic has been round for some time, however it’s nonetheless one of many prime an infection vectors!
- Improve Worker Coaching: Transcend fundamental consciousness. Implement common, interactive cybersecurity simulations and scenario-based coaching.
- PATCH OR DIE!
- Implement a Multi-layered safety and protection in depth posture.
- Undertake a Complete Backup Technique: Implement the 3-2-1 backup rule with immutable backups to guard towards ransomware assaults.
- Develop and Check Incident Response Plans: Create, frequently replace, and apply cybersecurity incident response plans.
Particular person Customers:
- Use Password Managers: Make use of a good password supervisor to create and retailer sturdy, distinctive passwords for all accounts – contemplate passphrases.
- Allow Multi-Issue Authentication (MFA): Activate MFA on all accounts that provide it, ideally utilizing authenticator apps or {hardware} keys.
- Maintain Software program Up to date: Allow automated updates to your working system, functions, and safety software program.
- Be Cautious with Good Gadgets: Safe your IoT gadgets by altering default passwords and conserving firmware up to date.
- Observe Protected Social Media: Be cautious in regards to the private info you share on social media platforms.
- Use Digital Personal Networks (VPNs): Make use of a dependable VPN service, particularly when utilizing public Wi-Fi networks.
Obtain the infographic HERE




