Encryption is the method of changing readable data right into a secret code to guard it from unauthorized entry. Solely people with the right key can decrypt the information and restore it to its unique type.
Cybercriminals are always trying to find their subsequent sufferer, and sadly, that could possibly be you. Actually, the variety of Individuals affected by information breaches surged within the first half of 2024, rising 490% yr over yr. An astonishing 1,078,989,742 individuals had been impacted, up from 182,645,409.
With information breaches occurring on a regular basis, defending your private data is crucial. That is the place encryption is crucial. So what’s encryption? It acts as a secret code to safeguard your delicate information, guaranteeing it stays unreadable to anybody missing the best key.
Out of your on-line banking to your social media accounts, encryption is like digital armor. However what precisely is encryption, and what does being encrypted imply? We talk about all of the ins and outs of encryption, explaining why it’s essential in your on-line security and how one can profit from utilizing it.
What Is Encryption?
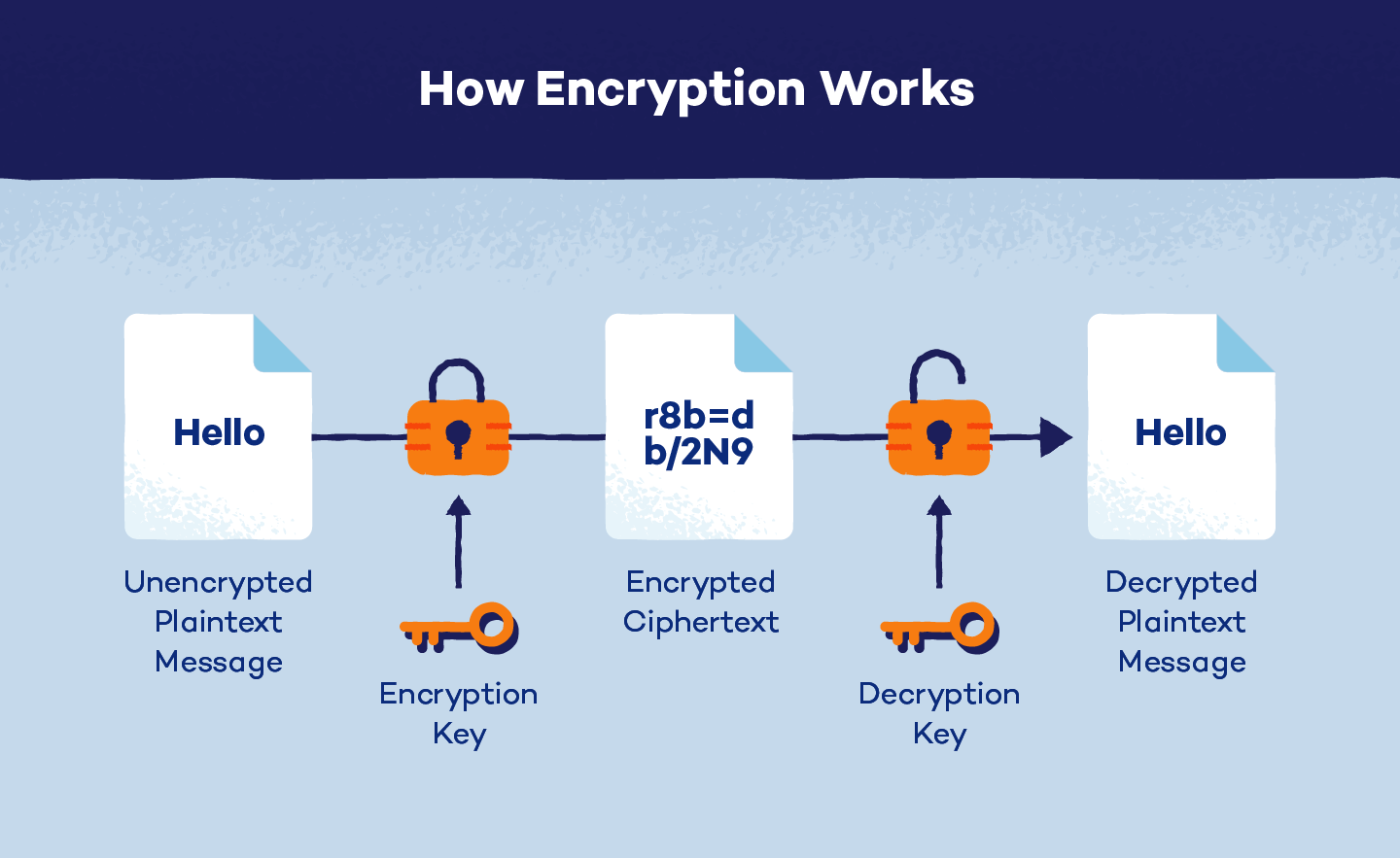
Encryption is the method of changing readable data (plaintext) into unreadable code (ciphertext). That is carried out utilizing complicated mathematical algorithms and a secret key. Solely people with the right key can decrypt the information and restore it to its unique type.
Consider it as locking a field with a novel key; with out the important thing, the contents stay inaccessible. In at the moment’s digital world, the place individuals always share delicate data on-line, information encryption is essential for safeguarding your information from unauthorized entry.
How Does Encryption Work?
Encryption takes your readable information and scrambles it into one thing that appears like gibberish known as ciphertext. Algorithms are the key formulation used for encryption. Encryption algorithms are just like the directions for scrambling and unscrambling the information.
Many various algorithms are on the market, corresponding to Information Encryption Customary (DES) and Superior Encryption Customary (AES), every with its personal stage of safety and goal.
So, there are two processes concerned right here:
- Encryption: Reworking plaintext into ciphertext utilizing a key and an algorithm
Decryption: Changing ciphertext again into readable plaintext To decrypt information, you want a particular key — distinctive codes that unlock the encrypted information. They are often quick or lengthy, and the size of the important thing determines how sturdy the encryption is. Longer keys are often more difficult to crack.
Consider it like a bodily key that opens a locked door. You want the right one to unscramble the ciphertext again into readable plaintext.
So, the following time you ship a safe e-mail or make a web based buy, keep in mind that encryption is working behind the scenes to guard your data.
Forms of Encryption
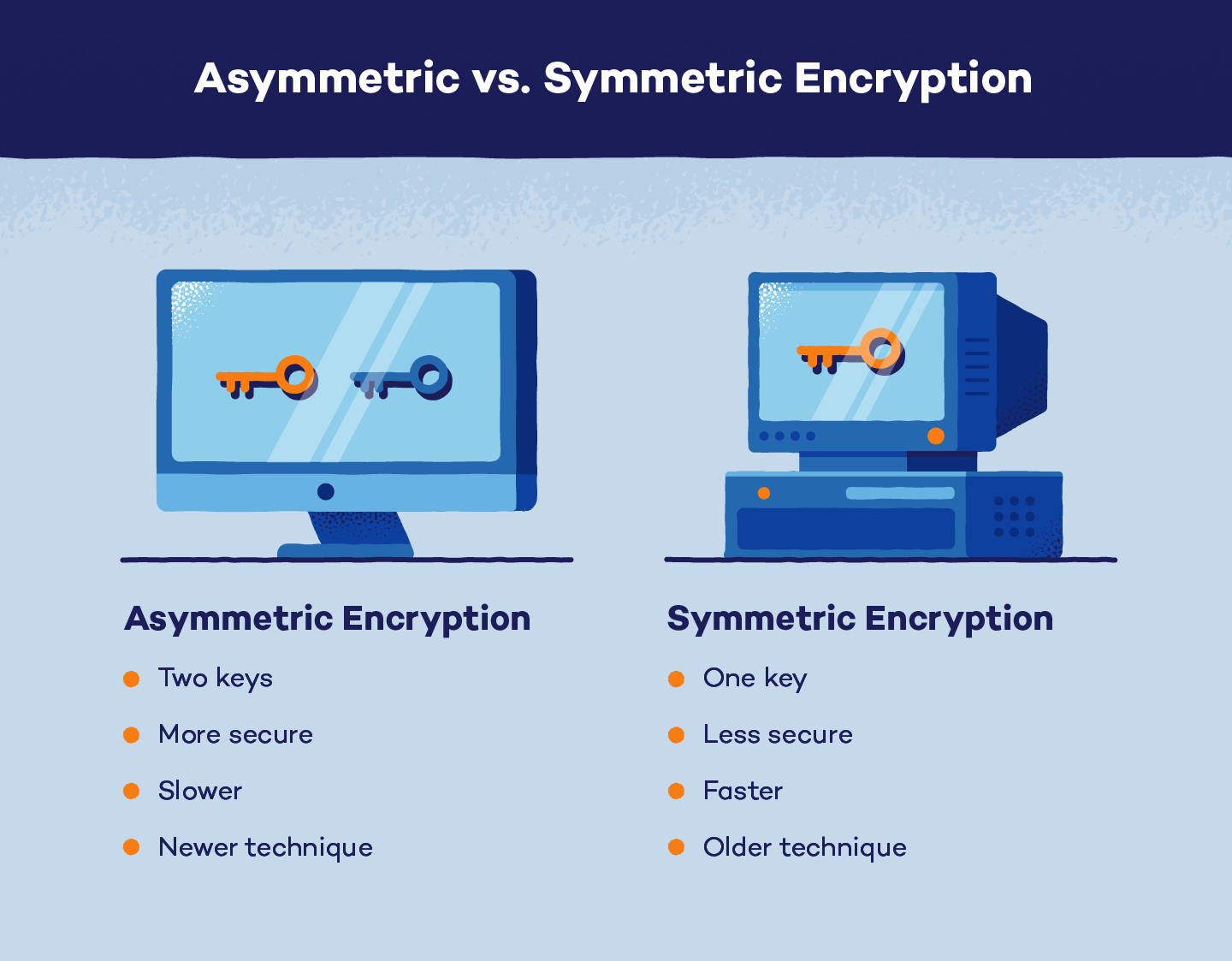
The 2 essential strategies of encryption are uneven and symmetric. Whereas each encryption strategies work in comparable methods, the distinction within the variety of keys units them aside.
Uneven Encryption
Uneven encryption, in any other case referred to as public key encryption or cryptography, depends on two completely different keys for encoding and decoding information. The general public key encrypts the plaintext, turning the message into ciphertext. The personal key decrypts ciphertext, returning it to plaintext.
The general public secret is obtainable for anybody, however every personal secret is particular for that recipient. Since two completely different keys are required, uneven tends to be a safer technique of encryption. It is because the encoded message can solely be decrypted with the personal key. Nevertheless, it’s a slower course of.
RSA is a typical uneven encryption algorithm broadly utilized in real-world purposes. A typical use case of this algorithm is securing data despatched over the web and collected by web sites in SSL certificates, which create an HTTPS connection.
Symmetric Encryption
Symmetric encryption makes use of only one personal key to encrypt the plaintext and decrypt ciphertext information.
In comparison with uneven encryption, symmetric encryption is much less safe, with just one key, and is faster to run. One other drawback is that since there is just one secret key, all events who want entry to the plaintext message should alternate the important thing earlier than decryption.
Some symmetric encryption algorithms, like DES, had been outdated and changed with AES and Triple DES. This type of encryption is commonly utilized in on-line fee purposes and random quantity era.
Why Encryption Issues
We hope (by now) you perceive that encryption is extra than simply technical jargon; it’s an important defend defending your digital life. Right here’s why it issues:
- Protects delicate information from unauthorized entry: Encryption acts as a digital lock, stopping hackers and cybercriminals from stealing your private data, monetary information and different delicate particulars.
- Ensures privateness in digital communications: Whether or not you’re sending emails, messaging buddies or making on-line purchases, encryption retains your conversations and transactions confidential.
- Prevents information breaches and cyber assaults: Encryption considerably reduces the chance of information breaches and cyberattacks by making information unreadable to unauthorized people.
- Builds belief with prospects and customers: When companies and people exhibit a dedication to information safety by way of encryption, it fosters belief and confidence.
Advantages of Encryption
Legend has it: Most individuals assume encryption is only for large firms and don’t trouble about it. In fact, it’s a strong instrument for safeguarding your private digital life, too. Listed below are some methods you’ll be able to profit from encrypted information:
- Protects private information: Out of your on-line banking to your social media profiles, encryption safeguards your delicate data from prying eyes.
- Secures on-line communications: Whether or not you’re emailing, messaging or video chatting, encryption ensures your conversations stay personal. Do not forget that encryption message from WhatsApp at first of a brand new chat?
- Prevents id theft: By defending your private data, encryption makes it considerably tougher for thieves to steal your id.
- Enhances system safety: In case your telephone or laptop computer is misplaced or stolen, encryption helps defend your information from falling into the improper arms.
Potential Drawbacks of Encryption
Whereas encryption is a strong instrument for safeguarding information, it’s not with out its challenges:
- Lack of encryption key: In case you lose or neglect the encryption key, the information turns into completely inaccessible, even in case you are the rightful proprietor.
- Elevated system complexity: Implementing and managing encryption might be complicated and requires specialised data, doubtlessly rising prices and system overhead.
- Efficiency influence: Encryption can decelerate system efficiency, particularly for resource-intensive duties.
- Potential for misuse: Unhealthy actors can use encryption to hide illicit actions, making it troublesome for legislation enforcement to research crimes.
- Susceptibility to brute power assaults: Whereas sturdy encryption algorithms are extremely resistant, weak encryption strategies might be susceptible to brute power assaults (unhealthy actors use a hit-and-trial system to guess your password).
- Ransomware danger: Malicious actors can goal encrypted information in ransomware assaults, holding it hostage till a ransom is paid.
Widespread Encryption Algorithms
A number of encryption algorithms exist for various circumstances. The most typical algorithms are:
- Information Encryption Customary (DES): An unique and fewer safe type of encryption not often used at the moment for safeguarding personal data.
- Triple DES: The unique DES technique ran thrice over to strengthen the encryption additional. It makes use of three keys, every with 56 bits, and is most generally utilized in monetary providers.
- Superior Encryption Customary (AES): Runs 128, 192 and 256-bit keys and is taken into account probably the most safe encryption algorithm at the moment obtainable. AES is the trusted normal for the U.S. authorities and different personal sectors.
- RSA: A public-key encryption algorithm standardly used for securing information shared through the web. RSA is powerful, dependable and in style.
- TwoFish: A quick and free encryption algorithm generally utilized in {hardware} and software program purposes.
Every algorithm requires a selected variety of keys to find out which sort of encryption is in place.
Encryption is your digital bodyguard, defending your delicate data from the ever-growing on-line threats. By understanding the fundamentals of how encryption works, you may make knowledgeable selections about safeguarding your private information. Slightly data goes a good distance in defending your digital life.
Along with your data, instruments like a VPN will help improve your on-line safety. A VPN provides an additional layer of safety by encrypting your web visitors and masking your IP handle. Stop hackers from intercepting your information and defend your privateness on-line with Panda Dome VPN.
Encryption FAQ
Nonetheless have questions on encryption? We’ve acquired solutions.
What Is an Instance of Encryption?
An on a regular basis instance of encryption is sending a safe e-mail. The content material of your e-mail is scrambled into an unreadable format utilizing encryption. Solely the supposed recipient, with the right decryption key, can learn the message.
What Is a Key in Cryptography?
A cryptographic secret is a chunk of knowledge, typically a string of numbers and letters, used to encrypt and decrypt information. It’s important for safeguarding data, because it acts like a digital lock and key.
Is Encryption Protected?
Fashionable encryption strategies are extremely safe when carried out appropriately. Robust encryption algorithms like AES are just about unimaginable to crack with present computing energy. Nevertheless, the safety of encryption depends upon components like key size and consumer practices.
Can Hackers Entry Encrypted Information?
Whereas hackers can theoretically entry encrypted information, breaking sturdy encryption is extraordinarily troublesome and infrequently impractical. Use sturdy, distinctive passwords and preserve your software program up-to-date to guard in opposition to different kinds of assaults.
Do You Have to Encrypt Your Pc?
Encrypting your pc is extremely beneficial, particularly if you happen to deal with delicate data. It protects your information from theft or unauthorized entry in case your system is misplaced or stolen.



