OAuth (Open Authorization) is a normal for authorization that permits a third-party utility to acquire restricted entry to your account on an HTTP service, akin to a social media platform, with out sharing your password.
OAuth, or open-standard authentication, is a framework or protocol that permits client-operated functions safe entry to different servers and providers. With OAuth, you possibly can safely management this third-party entry to guard passwords and login credentials.
As you work together with web sites or web-based functions, like your social media accounts, third events could ask for permission to entry your protected info. For those who grant them permission, OAuth can shield your non-public info in case the third occasion experiences a breach or different emergency state of affairs.
Have you ever ever seen a pop-up asking for permission to submit in your social media feed, entry your good gadgets or share recordsdata throughout totally different platforms? If sure, you’ve most certainly used OAuth already. However what precisely is OAuth, and the way does it work? Is it secure to make use of this framework? Let’s discover out — and extra!
What Is OAuth?
OAuth (vaguely termed OAuth authentication) is a safe technique to give apps entry to your info on different web sites. The very best half? You don’t need to share your password. Think about you desire a health app to entry your exercise knowledge on a separate well being app. With OAuth, you possibly can grant the health app permission to entry that particular knowledge with out giving it your login credentials for the well being app.
That mentioned, individuals typically marvel: Is OAuth authentication or authorization? Regardless of the identify, OAuth is about authorization, not authentication. Authentication apps like Google Authenticator confirm who you might be (like checking your ID at a retailer). Authorization determines what you are able to do when you’re verified (like granting entry to particular sections of the shop). OAuth focuses on the latter, letting you management what elements of your knowledge apps can entry on different platforms.
How Does OAuth Work?
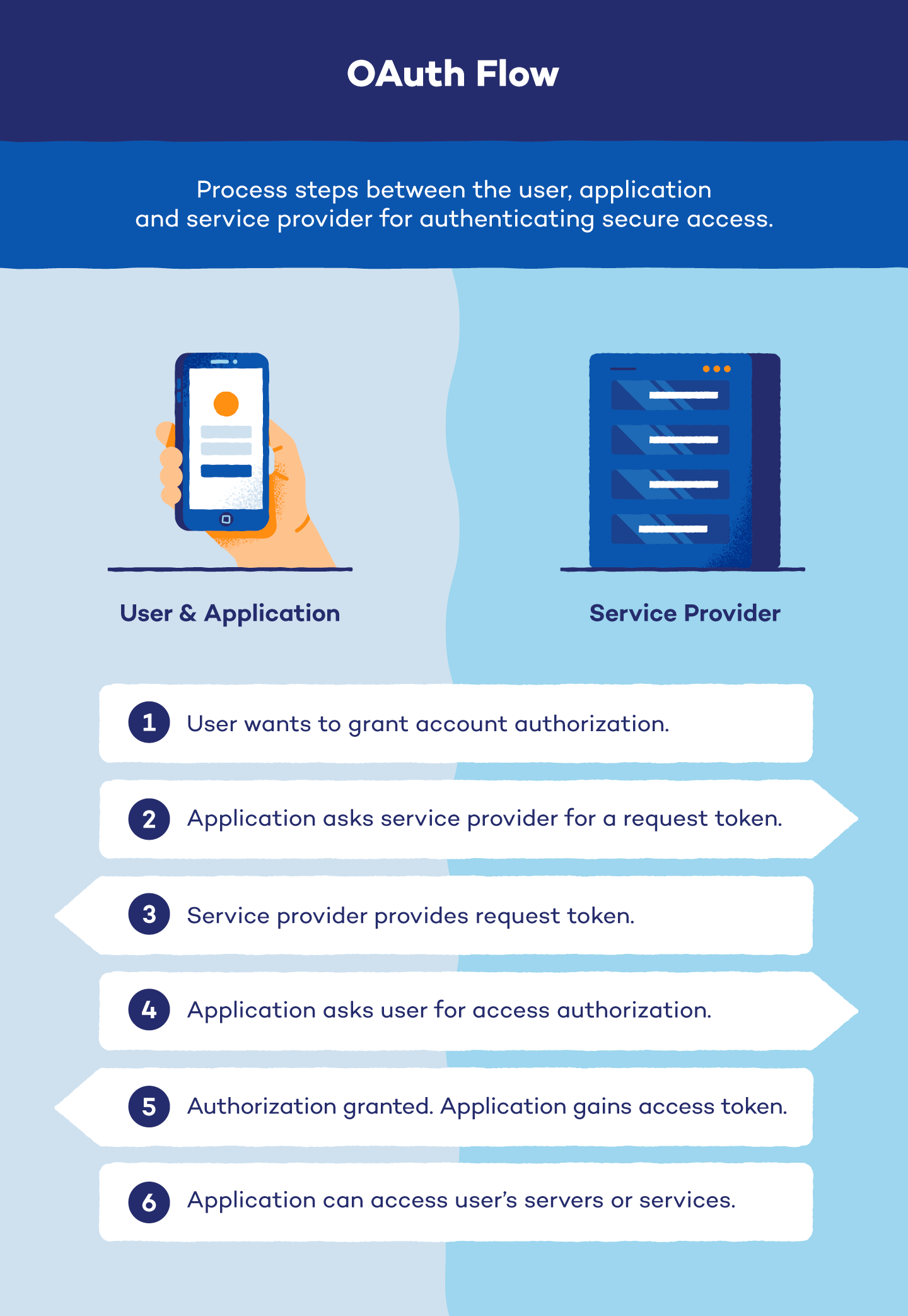
After you’ve given a 3rd occasion entry to your account, a six-step OAuth course of begins routinely. There are three teams concerned on this course of, often known as OAuth move: the person, the third occasion known as the applying and the service supplier.
Typically, the person is the unique proprietor of the profile in query, the applying is who desires entry to the profile and the service supplier is the place the profile in query resides.
Steps in OAuth move:
- Reveal intent: The person reveals that they need to give permission to an utility to entry protected servers or providers. This intent is most frequently revealed throughout interactions with social media apps or file sharing throughout techniques.
- Ask for service supplier’s permission: The appliance requests permission from the service supplier for authorization. Whether it is granted, the service supplier offers the applying a request token and shares a randomly generated password often known as a secret with the person. The person will signal every authentication request with the key so the service supplier can confirm they’re actually making the request.
- Be redirected: The appliance offers the person the request token. They’re then redirected to the service supplier to supply utility authorization.
- Ask for person permission: The person authorizes the request token. When licensed, the applying returns to the service supplier with out pharming for passwords or usernames. The service supplier will ask the person what permissions to grant and approve the request token.
- Acquire entry token: The appliance exchanges its request token for an entry token and secret from the service supplier.
- Entry person profile: Each time the applying accesses the person’s servers or providers, it should current its entry token and secret to the service supplier.
As a substitute of divulging password info to third-party customers, OAuth makes use of tokens to authorize a person’s id, their connection to an account and their service suppliers. An OAuth token is safer than sharing password info and can be protected by a secret recognized solely by the person, utility and repair supplier.
SAML vs. OAuth
Safety Assertion Markup Language (SAML) is commonly in comparison with OAuth. The previous could be known as OAuth’s “older sibling” due to the similarities between the 2 packages. As a result of SAML makes use of XML and cookies to provide customers entry to net maps whereas each authenticating and authorizing credentials, it will definitely turned too outdated for high-tech cellular, net and gaming functions.
Whereas these two protocols share some similarities, there are a number of vital variations between them.
Variations Between OAuth and SAML
| OAuth | SAML | |
|---|---|---|
| Definition | Open-standard authentication framework for customers and functions | Open customary that passes authorization credentials to service suppliers |
| Format | JSON | XML |
| Person Expertise | Makes use of API calls to supply a easy cellular expertise | Makes use of session cookies for enterprise safety |
| Greatest Used For | Cell apps, fashionable net apps, recreation consoles and Web of Issues (IoT) gadgets | Single sign-on functions |
OAuth 1.0 vs. OAuth 2.0
Whereas OAuth is a normal authentication framework, there have been totally different variations of its protocols. OAuth 1.0 is the unique open-standard authentication framework, whereas OAuth 2.0 is the newer, extra mainstream model. As a result of OAuth 2.0 was anticipated to interchange older variations of the framework, 1.0 and a couple of.0 are incompatible. Nevertheless, web sites can help each variations of OAuth, despite the fact that there are main variations between the 2.
| OAuth 1.0 | OAuth 2.0 |
|---|---|
| Safer than OAuth 2.0 | Supported by extra websites and gadgets |
| No OAuth token expiration | Much less safe than OAuth 1.0 |
| Much less complicated than OAuth 2.0 | Request tokens are short-lived whereas refresh tokens last more |
| Makes use of cryptographic necessities for the transmission of tokens and secrets and techniques | Doesn’t help encryption, signatures or channel binding |
| Solely helps three flows that don’t cowl non-browser or cellular system functions | Person wants a secondary safety protocol like Transport Layer Safety (TLS) |
| Secret signatures are easier |
OAuth 2.0 is the extra broadly accepted model of the framework. Many high-level web sites and consultants encourage customers to make this their customary authentication protocol because it affords a safer, versatile and user-friendly authorization expertise in comparison with OAuth 1.0.
OAuth Examples
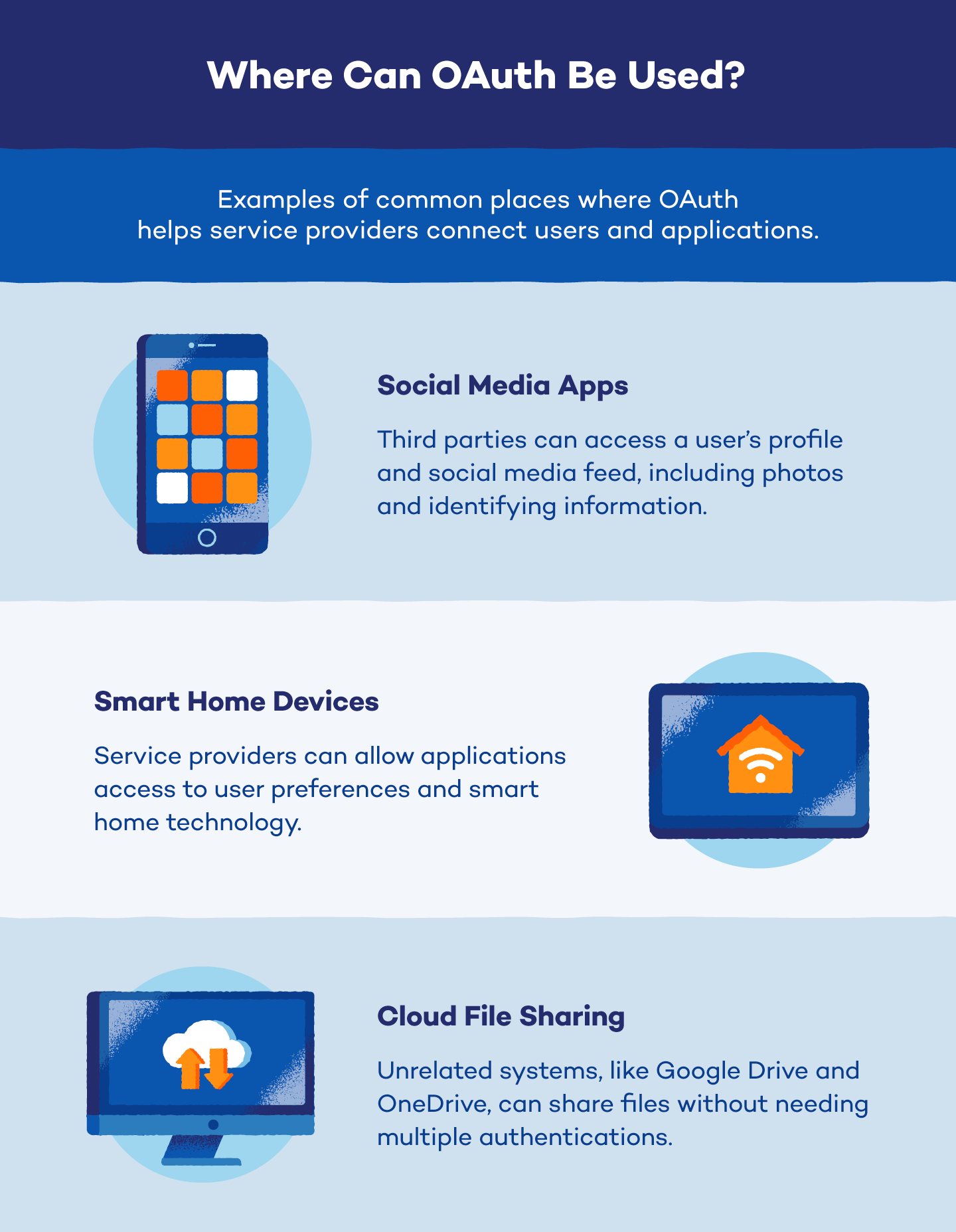
Third-party functions have began utilizing OAuth to entry person profiles, submit to accounts and log in to web sites and cellular functions extra often. Listed here are a couple of examples of how you need to use OAuth with social media apps, good dwelling gadgets and the cloud to share recordsdata. Whereas these characterize a number of the most typical makes use of of OAuth, the protocol finds utility in numerous different areas as effectively.
Social Media Apps
Social media platforms like Fb retailer person profiles and management entry to that knowledge. To entry this info, exterior apps want an OAuth token (and secret) granted by the platform. This ensures customers management what knowledge is shared and prevents apps from accessing unauthorized info.
For instance, in order for you an app like ESPN to submit updates in your Fb, it wants Fb’s permission. Fb grants entry tokens after you authorize the request, retaining your login credentials safe.
Sensible Dwelling Gadgets
Sensible dwelling gadgets, like Nest Studying Thermostat, management person knowledge and require OAuth for safe entry. This ensures third-party apps get licensed person permission earlier than accessing info like temperature settings or controlling your private home, akin to turning lights on or off based mostly on safety alerts.
Cloud File Sharing
Sharing cloud recordsdata throughout platforms could be difficult with out OAuth. Let’s say you need to share your Google Drive wedding ceremony album with dad and mom utilizing Microsoft OneDrive. OAuth permits you to securely grant entry with out them needing further accounts.
Whereas cloud storage encrypts content material, OAuth provides one other layer of safety when sharing knowledge. Nevertheless, each platforms have to help the identical OAuth model for a clean connection.
OAuth FAQ
Bought OAuth questions? We’ve obtained solutions! Dive into this FAQ part to study extra about how OAuth works and the way it retains your knowledge secure.
Is OAuth Protected?
There may be but to be a wonderfully secure resolution to retaining passwords and credentials safe when offering third events with authenticated entry. Nevertheless, utilizing OAuth (particularly OAuth 2.0) can considerably improve safety throughout the authentication and authorization processes. Plus, combining OAuth with Transport Layer Safety (TLS) or Safe Sockets Layer (SSL) can additional improve the security of credential authentication.
What Is OAuth Used For?
OAuth is used for safe authorization as a substitute of sharing passwords. It permits apps to entry your private info on different platforms together with your permission. This fashion, you management what knowledge is shared and preserve your passwords safe.
What Is the Distinction Between OAuth and Normal Authentication?
Let’s say you need to share your epic exercise playlist from Spotify together with your health teacher. With a normal login, you’d have to provide them your password! OAuth login permits you to grant the trainer entry to your Spotify playlist straight with out ever revealing your password. They get what they want, and your login stays safe.
What Is OAuth Token?
An OAuth token is a digital key that lets licensed apps entry particular elements of your knowledge on different platforms. Think about you’ve a home occasion — OAuth tokens are like visitor passes.
After studying “What’s OAuth?” you might be questioning how you can keep away from being hacked or dropping your login credentials. With out correct authentication and authorization practices, it’s simpler for out of doors forces to hack your accounts utilizing man-in-the-middle assaults and different credential-stealing assaults.
Being proactive and understanding your safety setting is the easiest way to keep away from cyberattacks that steal your credentials. Safe your community and web entry by investing in a VPN with Panda Safety, and follow password safety by utilizing our password supervisor.



