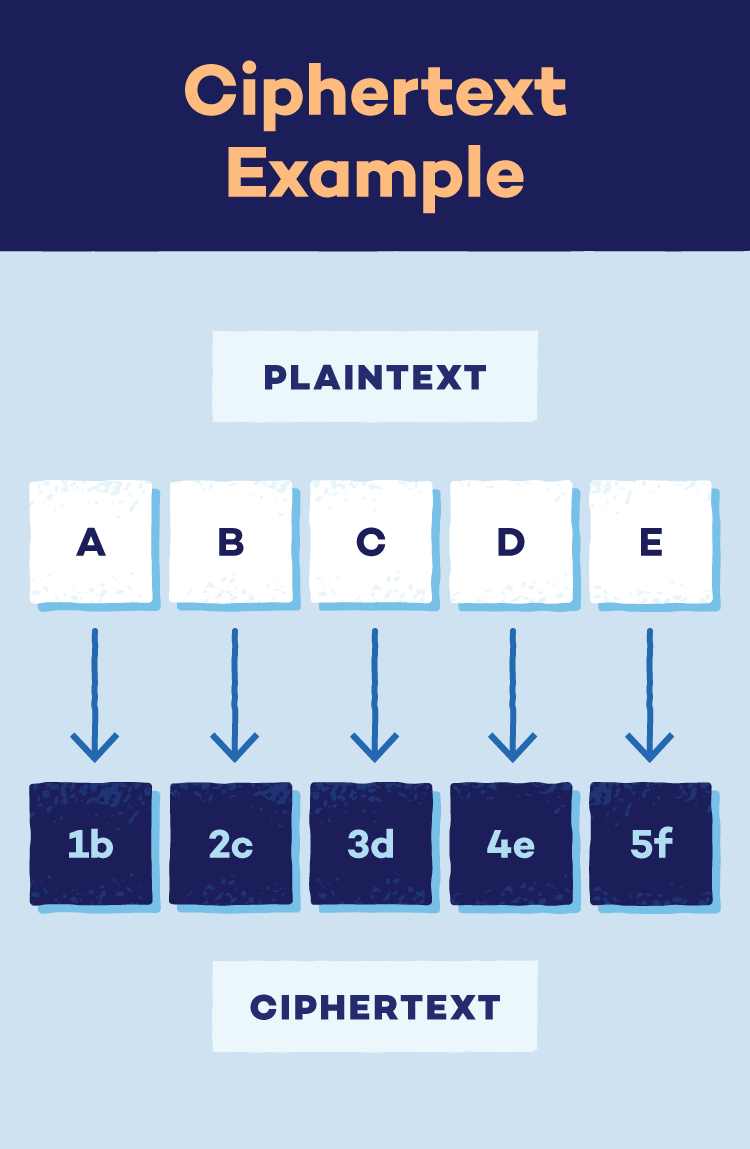
The Superior Encryption Customary (AES) is an algorithm that makes use of a robust password (secret key) to scramble your recordsdata and messages, making them unreadable to anybody who doesn’t have the important thing.
Whether or not or not it’s sending and receiving emails, transferring recordsdata or just shopping the online, information switch exists all over the place in our technological world.
In an age by which cybercriminals are attempting to entry that information at each flip, companies and shoppers alike have to be protected — and step one is to be taught what AES encryption is.
AES encryption is an encryption methodology that has grow to be the business normal resulting from its safety, ease of use and velocity. On this article, we are going to element what AES encryption is, the way it works and the way Panda can equip you with this beneficial safety methodology through a VPN and password supervisor.
What Is AES Encryption?
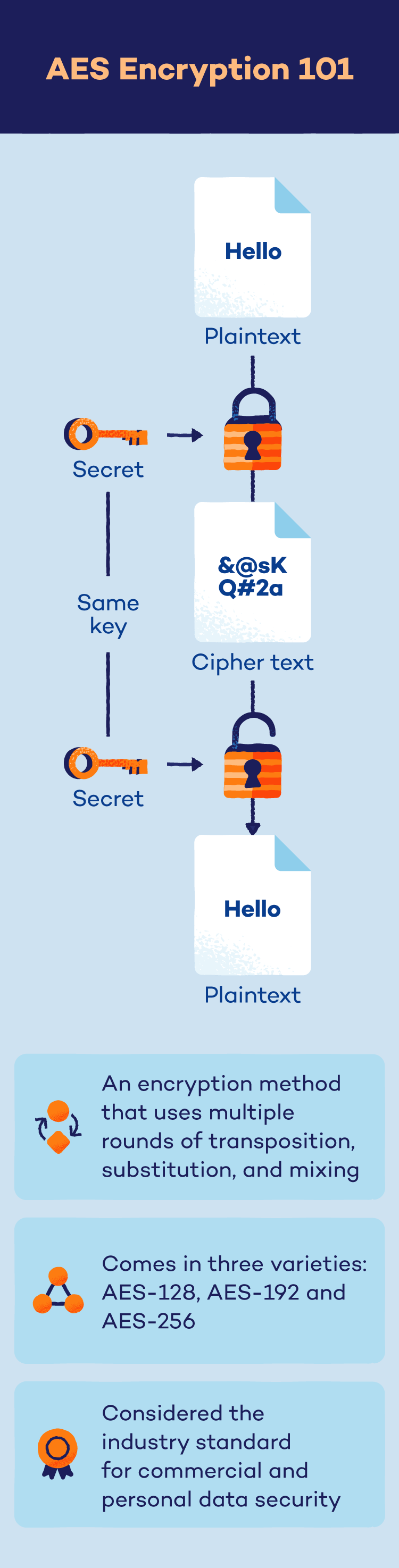
The Superior Encryption Customary (AES) is a strong algorithm established by the U.S. authorities to electronically safe delicate information. It makes use of a secret key to scramble info into an unreadable format, rendering it ineffective with out licensed entry.
Extensively adopted by the U.S. authorities, companies and people, AES safeguards vital info throughout storage or transmission. This ensures confidentiality even when information is intercepted by unauthorized events.
This methodology was first conceptualized in 1997 when the Nationwide Institute of Requirements and Expertise (NIST) turned susceptible to brute pressure assaults and wanted a stronger encryption methodology. NIST enlisted a pair of builders to deal with the issue — Vincent Rijmen and Joan Daemen — who developed the ultimately chosen know-how, AES, in 1998.
AES has been the encryption normal for the NIST since its full-scale adoption in 2002. Total, there are three foremost varieties of AES encryption:
- AES-128: This methodology makes use of a 128-bit key size for encryption and decryption, which leads to 10 rounds of encryption with 3.4 x 1038 totally different potential combos.
- AES-192: This methodology makes use of a 192-bit key size for encryption and decryption, which leads to 12 rounds of encryption with 6.2 x 1057 totally different potential combos.
- AES-256: This methodology makes use of a 256-bit key size for encryption and decryption, which leads to 14 rounds of encryption with 1.1 x 1077 totally different potential combos.
What Is AES Used For?
Though AES was first formulated at the side of america authorities, this encryption methodology is now utilized in each governmental and civilian purposes. Just a few of the commonest makes use of of AES encryption embody:
- VPNs: The job of a digital non-public community (VPN) is to offer safe and personal on-line shopping. Since this course of connects customers to totally different servers, AES encryption is used to guard person information towards leaks and cyberattacks.
- Password managers: Password managers are used to securely retailer login credentials beneath a single grasp key. Given a single breach may compromise a person’s complete assortment of passwords, AES is commonly used to safe this software program.
- Wi-Fi: Wi-fi web sometimes makes use of many encryption strategies corresponding to WPA2, and AES can usually be present in these connections as properly.
- Cell apps: Any app that includes messaging or picture sharing sometimes makes use of AES to assist in information safety.
- Web browsers: Once you go to a web site that makes use of HTTPS, the communication between your browser and the web site is encrypted utilizing AES. This protects delicate info you ship or obtain, corresponding to bank card particulars or login credentials, from being intercepted by hackers.
- Databases: Databases usually retailer confidential info, like medical information or monetary information. AES can be utilized to encrypt this information at relaxation (when saved on a server) or in transit (when transferred between programs). This ensures that even when somebody positive factors entry to the database, they can’t decipher the knowledge with out the decryption key.
- Safeguarding delicate recordsdata: You need to use AES to encrypt particular person recordsdata in your pc or different units. That is significantly helpful for defending private info corresponding to paperwork, images or monetary information. Encryption ensures that even when somebody steals your system or positive factors entry to your storage, they can’t entry the encrypted recordsdata with out the decryption key.
How Does AES Work?
Regardless of the kind of AES, the encryption course of is comparable and may be described in a sequence of steps:
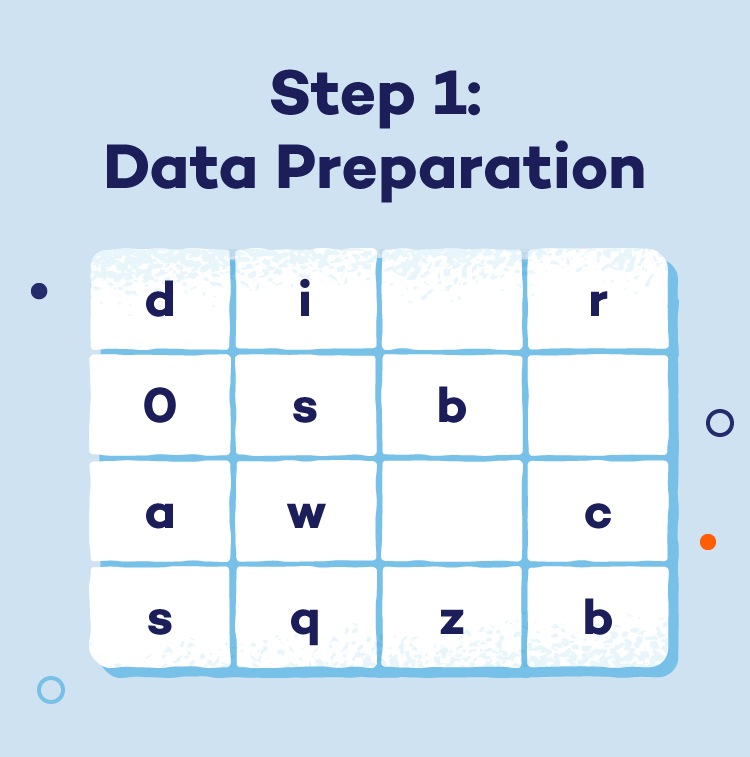
- Step 1: Knowledge preparation: AES divides the preliminary message (plaintext) into fixed-size blocks (sometimes 128 bits) for environment friendly processing.
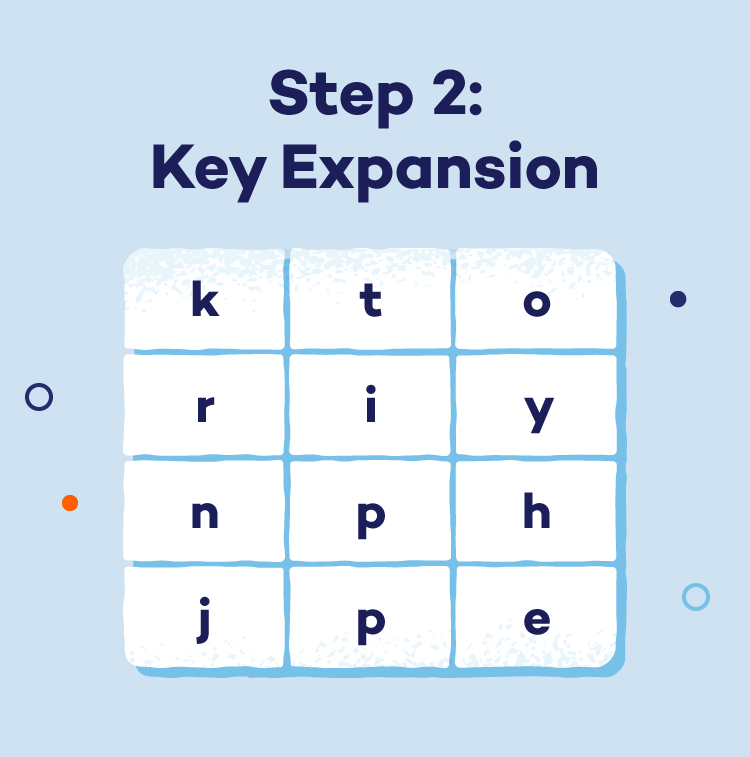
- Step 2: Key enlargement: A secret key, essential for each encryption and decryption, is used to derive a sequence of distinctive spherical keys. This enlargement course of enhances the general safety of the encryption.
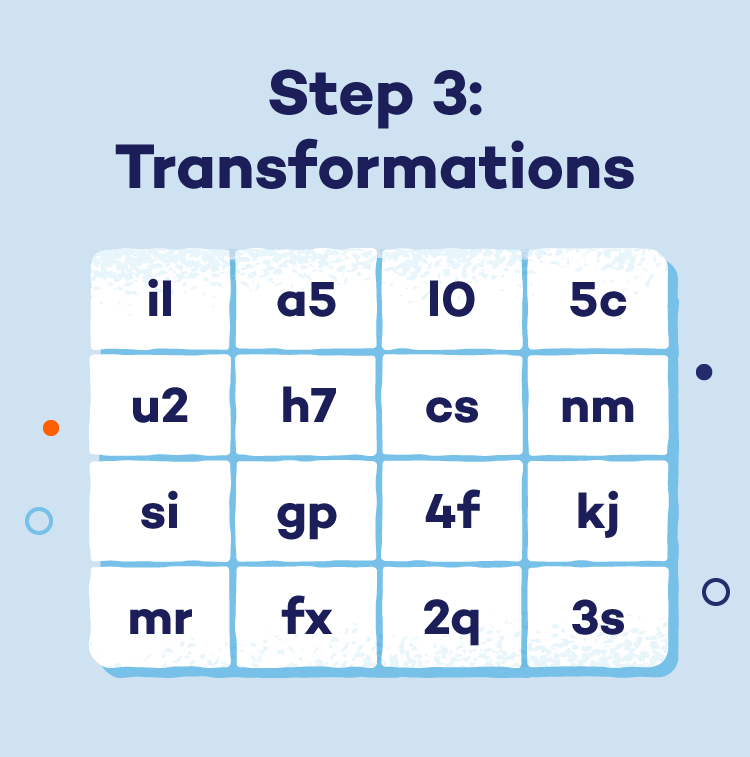
- Step 3: Transformations: Every information block undergoes a number of rounds of intricate transformations. (The variety of rounds depends upon the important thing size.) These rounds intention to totally confuse the info through:
- SubBytes: A predefined desk substitutes every byte within the block with a very totally different byte.
- ShiftRows: The rows of the info block are cyclically shifted to disrupt any patterns.
- MixColumns: A particular mathematical operation mixes the info inside every column, additional enhancing obfuscation.
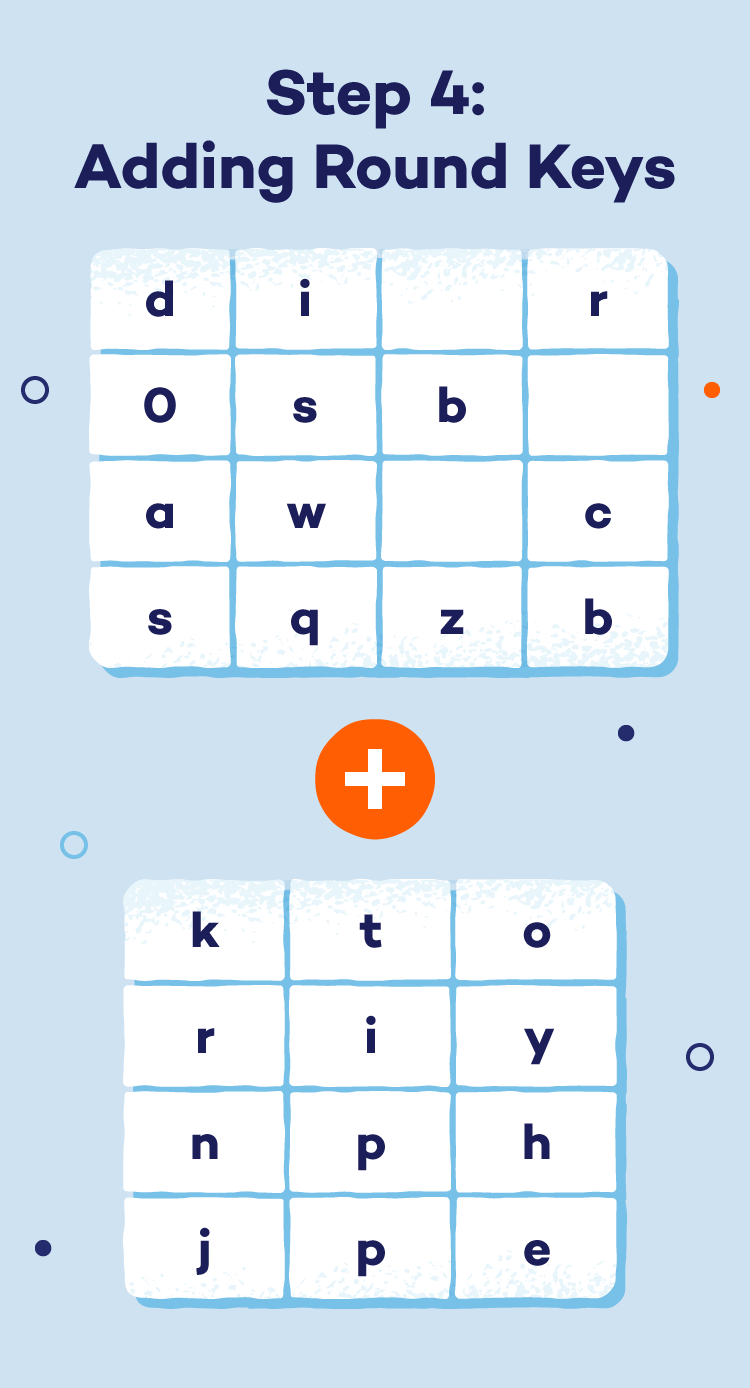
- Step 4: Including spherical keys: In every spherical, a distinct spherical key (derived from the unique secret key) is utilized to the info block. This provides one other layer of encryption with distinctive keys for every spherical.
- The end result: Encrypted information (ciphertext): After all of the rounds, the info blocks are reworked into an unreadable kind known as ciphertext. This ciphertext is what’s securely saved or transmitted. Deciphering it requires the corresponding secret key.
Benefits of AES Encryption
AES is the popular encryption methodology as a result of it excels in lots of key efficiency metrics. Just a few advantages of AES embody:
- Safety: Even the bottom stage of AES encryption, AES-128, would take an estimated 1 billion billion years (no, that additional billion isn’t a typo) to crack if utilizing a brute pressure methodology.
- Value: AES encryption is on the market without cost, because it was initially developed to be launched on a royalty-free foundation.
- Ease of use: The AES algorithm is straightforward to implement throughout a mess of purposes and is understood for its simplicity and skill to evolve throughout {hardware} and software program platforms.
AES Encryption Assaults
AES is a sturdy encryption algorithm extensively trusted for securing delicate information. Nonetheless, no safety measure is foolproof, and AES encryption continues to be vulnerable to assaults, together with:
- Aspect-channel assaults: These assaults exploit weaknesses within the implementation of AES fairly than the algorithm itself. They could goal info leaks throughout encryption, corresponding to processing time fluctuations or energy consumption. By analyzing these leaks, attackers may doubtlessly glean clues concerning the secret key.
- Brute pressure assaults: This assault includes attempting each single potential key mixture till the right one is discovered.
- Associated-key assaults: These assaults are much less frequent and require a selected situation by which an attacker has entry to a number of units of information encrypted with associated keys. By analyzing the relationships between the ciphertexts, they might theoretically achieve insights into the important thing itself. Nonetheless, this requires a really particular scenario and isn’t a typical risk for many customers.
The best way to Stop AES Encryption Assaults
Whereas AES encryption is highly effective, a layered safety strategy is essential. Right here’s how one can reduce the chance of assaults:
- Create robust passwords: When utilizing AES encryption (usually present in disk encryption software program or password managers), select lengthy and complicated passwords to your encryption keys. Think about your key as a gatekeeper — the stronger and extra intricate, the tougher it’s to interrupt in.
- Software program updates matter: Maintain your software program up-to-date, particularly safety purposes and disk encryption instruments. Updates usually embody patches for vulnerabilities that may very well be exploited in AES implementations.
- Secrecy is vital: By no means share your encryption keys with anybody, and be aware of the place you retailer them. Keep away from conserving them on the identical system you’re encrypting. Think about using a password supervisor with robust security measures.
- Use multi-factor authentication: Implement multi-factor authentication (MFA) at any time when potential. MFA provides an additional step to the login course of, requiring a second verification issue past your password. This makes it considerably tougher for attackers to entry your encrypted information, even when they acquire your password.
How Does AES Examine to Different Encryption?
Whereas AES is a powerful encryption methodology, how does it evaluate to different choices accessible? Right here is how AES stacks up towards related programs.
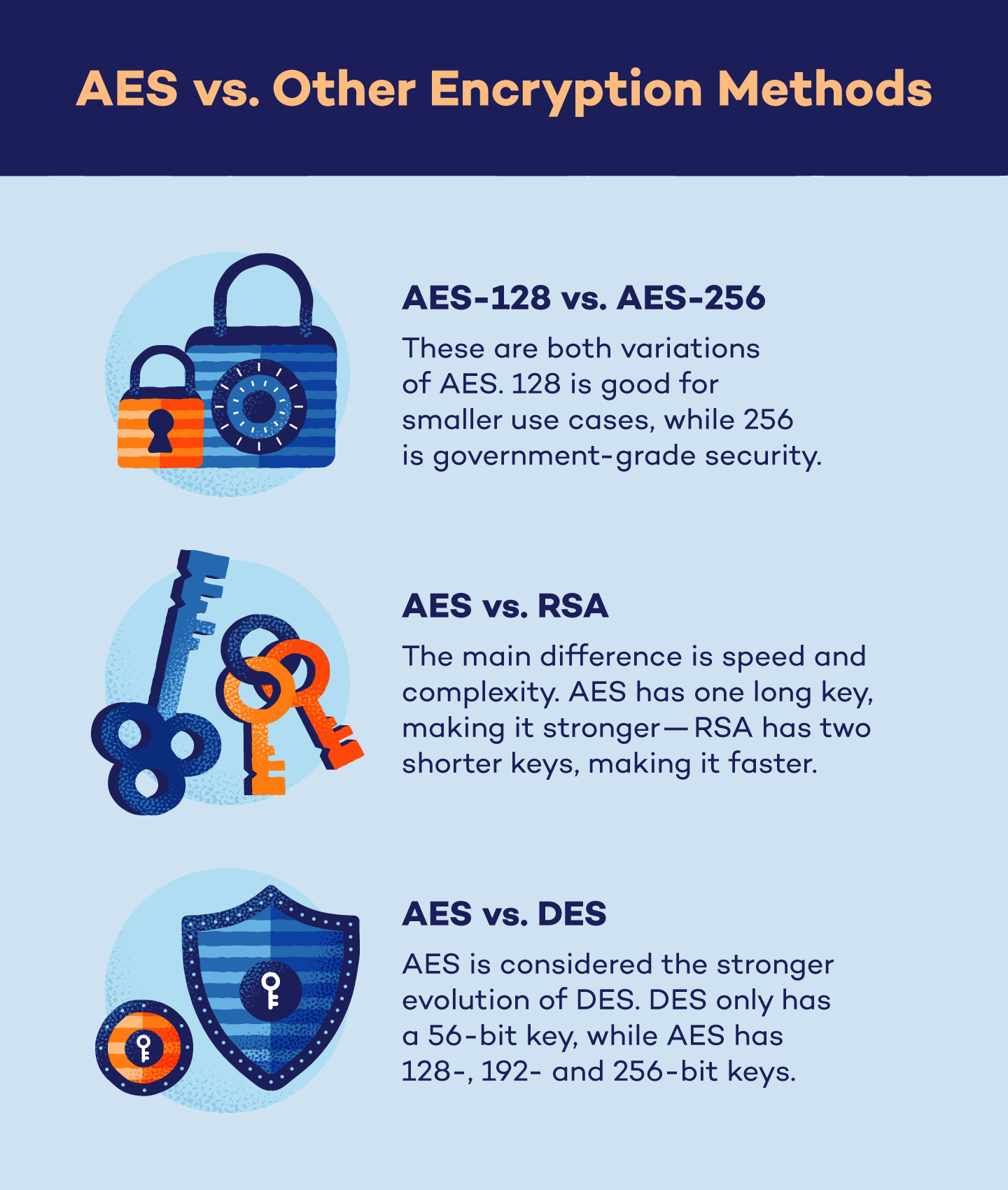
AES-128 vs. AES-256
AES-128 and AES-256 could seem to be two totally different programs, however they’re merely two variations of the identical encryption methodology.
AES-128 includes a 128-bit key size by which information goes by means of 10 rounds of encryption. Whereas this methodology is extraordinarily safe towards brute pressure assaults, it has the bottom safety specs of all AES variations.
AES-256 includes a 256-bit key size by which information goes by means of 14 rounds of encryption, and has the best safety specs of all AES variations. 256 is slowly being adopted into on a regular basis use resulting from steady developments in know-how.
AES vs. RSA
RSA, or Rivest, Shamir and Adleman, is a kind of encryption that makes use of an uneven algorithm to encrypt and decrypt information. This methodology may be paired with different encryption strategies corresponding to PGP encryption to generate a pair of associated keys — in any other case referred to as private and non-private keys.
Whereas each algorithms are safe, the primary distinction between AES and RSA comes down to hurry and complexity.
Since AES makes use of the identical key to encrypt and decrypt information, it’s extra user-friendly, cheaper and safer towards brute pressure assaults as a result of size of the password. RSA, however, is quicker in processing information as a result of the size of the keys are shorter.
Regardless of their variations, each AES and RSA are dependable strategies to encrypt and safe information.
AES vs. DES
DES, or information encryption normal, is the now-outdated encryption methodology utilized by authorities businesses beginning within the Seventies.
DES and AES are related in performance, however the distinction is solely that AES is extra environment friendly and safe. Whereas DES makes use of a 56-bit key, AES makes use of 128-, 192-, and 256-bit keys which leads to elevated safety. AES can also be quicker than DES, leading to faster encryption.
Total, AES has changed DES in practically each capability.
AES Encryption FAQ
Lastly, we are going to wrap up with just a few continuously requested questions on AES encryption.
Is AES Symmetric or Uneven?
AES is classed as a symmetric encryption algorithm. Which means the identical secret secret’s used for each encrypting and decrypting information. This symmetric strategy gives benefits by way of velocity and effectivity, particularly when coping with giant information volumes. Nonetheless, it additionally necessitates cautious key administration. Anybody who possesses the key key can decrypt the info, making it essential to maintain the important thing safe.
What Is AES 128 vs. 192 vs. 256?
AES 128, 192 and 256 are all variations of the identical algorithm, however the distinction lies in the important thing size and rounds of encryption.
AES-128 makes use of a 128-bit key size for encryption and decryption, which leads to 10 rounds of encryption; AES-192 makes use of a 192-bit key size for encryption and decryption, which leads to 12 rounds of encryption; and AES-256 makes use of a 256-bit key size for encryption and decryption, which leads to 14 rounds of encryption.
Is 128-Bit AES Safe?
Sure, 128-bit AES is safe. In reality, if utilizing brute pressure strategies, it could take 1 billion billion years to crack.
Is AES Free to Use?
Sure, AES is free to make use of. It was initially developed to be launched on a royalty-free foundation.
Is AES the Finest Encryption Methodology?
The very best encryption methodology for you depends upon what’s essential to your scenario. That mentioned, AES is without doubt one of the main encryption strategies in the marketplace, trusted by the Nationwide Institute of Requirements and Expertise since 2002.
Panda Safety Can Assist With Encryption
AES encryption is a particularly safe and user-friendly algorithm that may defend your most delicate information. Present in a variety of on a regular basis purposes, this methodology is the go-to for defending delicate information towards brute pressure assaults.
If you’d like the facility of AES encryption in your on a regular basis cyber exercise, enlist the assistance of Panda’s VPN and password supervisor companies to expertly safe your information towards cyberthreats.