Are you OK with a stranger studying your emails?
Most individuals would reply that query with a convincing “no” — however sadly, on this trendy technological age, it’s far too simple for cybercriminals to achieve entry to your e-mail accounts or the messages themselves. To ensure your data is protected from prying eyes, you want Fairly Good Privateness (PGP) encryption.
So what’s PGP? Briefly, it’s an encryption system that scrambles your knowledge, making it unreadable to anybody who doesn’t have the technique of decoding it. By coordinating and sharing digital keys, e-mail senders and receivers can guarantee their data stays non-public and safe.
On this article, we’ll element the fundamentals of PGP encryption: what it’s, how you should utilize it and if this know-how is best for you.
What Is PGP Encryption?
PGP is an encryption system that’s used to securely ship delicate or non-public data. First developed in 1991, this know-how has change into one of the well-liked encryption strategies available on the market resulting from its safety and accessibility.
PGP encryption is mostly used for sending and receiving confidential emails. Cybercriminals can simply intercept messages and entry e-mail accounts, and PGP ensures that the person’s data stays safe.
In an age the place cyberthreats lurk round each digital nook, any such encryption is a vital instrument for anybody who desires assured privateness of their digital communications.
How Does PGP Encryption Work?
PGP encryption works by scrambling, or encrypting, a message in a approach that makes it unreadable to anybody who lacks the means to decode it. With a purpose to totally perceive PGP encryption, we’ll have a look at it from a technical perspective and supply a sensible analogy.
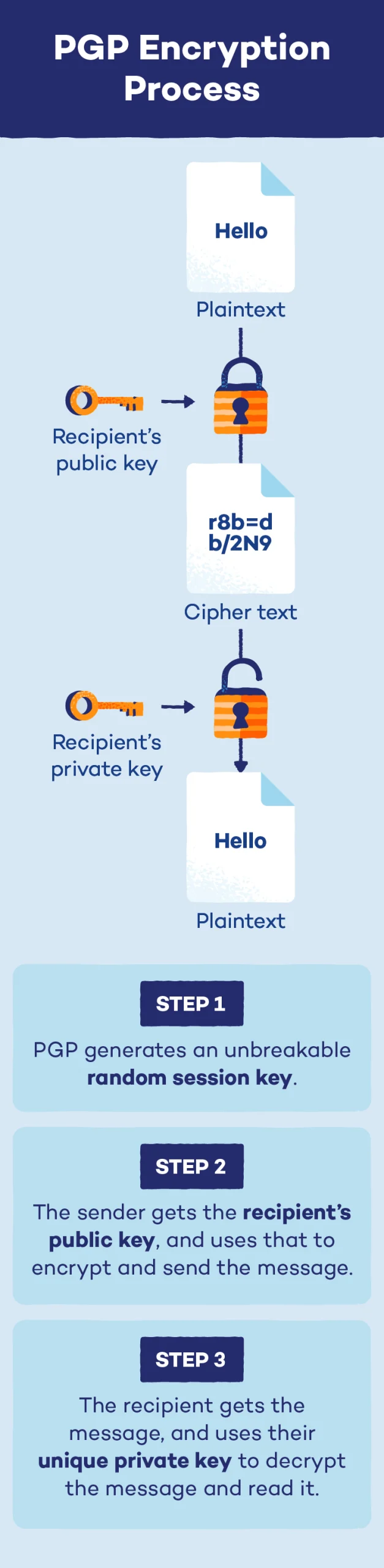
At a excessive technical stage, PGP encryption protects knowledge through the use of a mix of public keys, non-public keys and session keys.
When a person desires to ship a non-public e-mail or message, they’ll encrypt it utilizing the receiver’s public key — an encryption key that’s identified to everybody. As soon as the receiver will get the e-mail, they’ll decrypt it utilizing their non-public key — an encryption key that’s solely identified by one person. This ensures that the message will get the place it must go and that the recipient is the one one who can decrypt the message.
To sum it up, PGP encryption works in a three-step course of:
- Step 1: PGP generates a particularly complicated single-use random session key that can not be guessed.
- Step 2: This session secret is encrypted utilizing the recipient’s public key. This public secret is related to the person, they usually can share it with anybody they want to obtain messages from.
- Step 3: The sender passes alongside their session key, and the recipient can use their non-public key to decrypt and browse the message.
Now that we’ve walked via the technical facets of PGP, let’s have a look at an analogy to strengthen the idea:
- Michael desires to ship Beth a non-public message.
- In response, Beth sends Michael an open field (her public key) in addition to an open padlock (that solely she has the important thing for).
- Michael places the message within the field, closes it and locks it with the padlock. Now that the padlock has been closed, nobody however Beth (the proprietor of the non-public key) can open it.
- Michael sends the field to Beth, who opens it together with her non-public key.
As you possibly can see, with PGP encryption, Michael received’t have to fret in regards to the field getting misplaced or stolen in transit as a result of solely Beth has the means to open the lock.
On the finish of the day, that’s what makes PGP encryption so safe — and in addition why it’s crucial you don’t lose or share your non-public key in the event you’re sending encrypted recordsdata often.
How you can Use PGP Encryption
You need to use PGP encryption wherever you want an assurance of technological privateness. That mentioned, the three hottest methods of utilizing it are e-mail and file encryption and digital signature verification.
Encrypting Emails
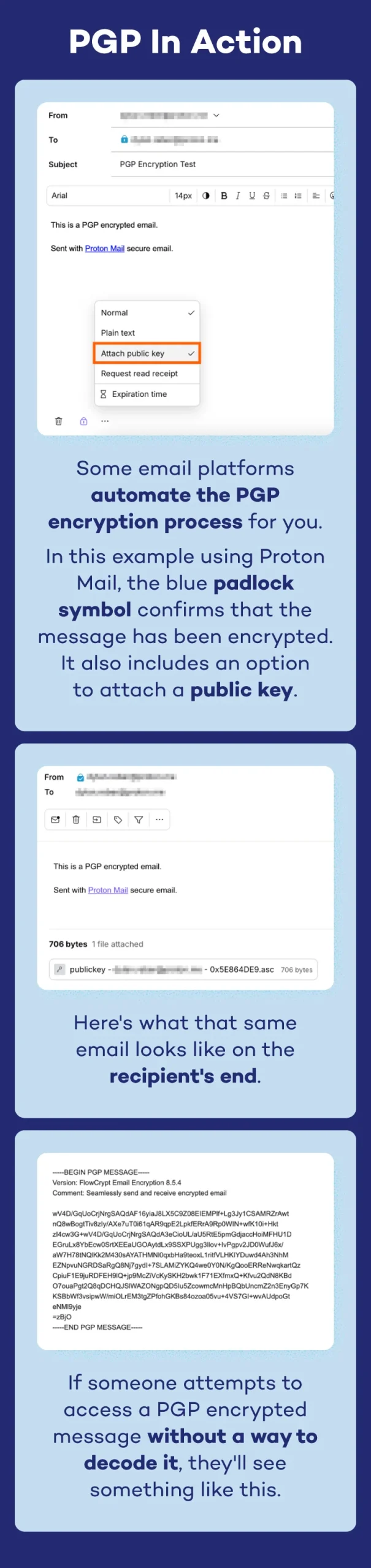
E mail messaging has change into one of the frequent methods of exchanging data, however this communication technique comes with dangers. Each e-mail accounts and the messages themselves can simply be intercepted by cybercriminals and different unauthorized people, resulting in potential knowledge leaks.
PGP encryption solves this drawback by participating within the safe data alternate course of we outlined above. Defending emails is the commonest motive folks use PGP encryption. Right here’s what it seems to be like in motion:
Encrypting Recordsdata
As a result of the complexity of the PGP algorithm makes it just about unbreakable, this encryption technique can also be helpful for securing private recordsdata.
People can use PGP to encrypt recordsdata on their laptop, flash drive, exterior exhausting drive or different storage gadgets. Paired with risk detection and response instruments, PGP file encryption helps preserve your private data non-public.
Digital Signature Verification
By means of PGP, people may make sure the authenticity of digital paperwork by verifying the id of the sender and confirming that the knowledge within the message has not been tampered with.
These digital signatures work by producing and encrypting a hash of the message, or a set block of knowledge, when it’s despatched. The recipient of the message can entry this knowledge via the usage of private and non-private keys, and they’ll be capable of see if the message has been altered or in any other case manipulated.

Is PGP Encryption Proper for You?
PGP encryption is a strong instrument, however is it best for you? Beneath, we spotlight the professionals and cons of this know-how.
| Professionals | Cons |
|---|---|
| Unbreakable encryption | Software program could be complicated |
| Enhances cloud safety | Requires coaching |
| Low-cost and free choices | Not nameless |
Professionals of PGP Encryption
PGP encryption is a well-liked technique to maintain data safe — and for good motive. Just a few of the highest advantages of this know-how embrace:
- Unbreakable algorithm: PGP’s algorithm is just about unbreakable, which means your communications, recordsdata and different data is assured to be protected from unauthorized customers.
- Enhanced safety: Persistently utilizing PGP in communications will improve cloud safety, resulting in a safer on-line expertise for people and companies.
- Cheap: PGP software program is inexpensive, with a large number of low cost but efficient choices available on the market.
Cons of PGP Encryption
Whereas this know-how is extraordinarily efficient, there are nonetheless just a few downsides customers ought to concentrate on. Just a few of the cons of PGP encryption embrace:
- Complicated: PGP encryption is a sophisticated software program that may be troublesome and time-consuming to be taught.
- Requires coaching: To ensure safety, all customers should safeguard their non-public keys. If a person misplaces or by accident offers away this data, there’s actual potential for safety breaches and uncovered data.
- Can’t be nameless: All senders and recipients of data despatched with PGP could be traced, which means there is no such thing as a skill for anonymity with this encryption technique.
How you can Set Up PGP Encryption
Now that you just’re an professional on PGP, you will have determined to make use of the know-how in your communications going ahead. Fortunately, establishing and utilizing PGP is a straightforward course of.
Selecting a PGP Supplier
Step one is to pick out a PGP supplier. There are a lot available on the market — each free and paid choices — which are appropriate with Home windows, Mac, Linux, iOS and extra. OpenPGP and Gpg4win are two free choices with good opinions. Alternatively, you possibly can join an e-mail platform that makes use of PGP or set up a PGP browser extension.
Setting Up PGP
When you’ve downloaded the software program, you’ll generate your private and non-private keys instantly from the platform. From there, your e-mail consumer may have a brand new choice to simply encrypt the e-mail message — and with that, you’ll be speaking securely with PGP.
PGP Encryption FAQ
Lastly, we’ll wrap up with just a few ceaselessly requested questions on PGP encryption.
Is PGP Encryption Nonetheless Used?
Sure, PGP encryption continues to be used at this time. The truth is, it is likely one of the hottest safety strategies when sending delicate data over e-mail.
What Is a PGP Key?
PGP keys are available in three types: public, non-public and session. The session secret is a large quantity that can not be guessed, which is then encrypted by the general public key. The non-public key decrypts the PGP-encrypted message as soon as it has been delivered.
How Do I Get a PGP Key?
PGP keys could be generated utilizing PGP encryption software program. When you don’t wish to obtain a program, some e-mail platforms help PGP and might generate keys for you.
How Safe Is PGP?
PGP could be very safe. PGP encryption is a particularly complicated algorithm that can not be cracked, guaranteeing the security of your knowledge, e-mail communication and different data.
Is PGP Higher Than AES?
PGP is simply as efficient as AES (Superior Encryption Commonplace), and which one you select will depend on your preferences. The primary distinction is that AES makes use of the identical key to encrypt and decrypt, whereas PGP makes use of two completely different keys.
Panda Safety Can Assist With On-line Privateness
PGP encryption is a strong instrument you should utilize to guard emails, private recordsdata and different delicate data. That mentioned, on-line privateness doesn’t begin and finish with PGP — to realize complete safety, you’ll want to make sure that your gadgets and networks are protected.
At Panda Safety, we have now quite a lot of instruments similar to password managers, antivirus instruments and darkish internet scanners to make sure you keep protected regardless of the place you just about go to. Allow us to enable you to in your tech journey at this time.



