| Fast reply: Spoofing is a deceitful tactic the place a person or entity — corresponding to a scammer — masquerades as another person, normally with dangerous intentions.
Spoofing strategies embody forging e mail addresses, manipulating caller IDs or creating pretend web sites to trick people or programs into believing the spoofed entity is real, leading to unauthorized entry, knowledge theft or different opposed penalties. |
Think about you’re having fun with a quiet night at dwelling, searching the web, while you abruptly obtain an e mail claiming to be out of your financial institution, urgently requesting your private info to confirm your account. Alarmed, you swiftly comply, solely to comprehend later that you just’ve fallen sufferer to a intelligent scheme often known as spoofing. However what’s spoofing precisely, and the way does it work?
The implications of spoofing can lengthen far past mere inconvenience, resulting in compromised safety, identification theft and monetary loss. On this put up, we’ll go over what spoofing is, differing types and tricks to forestall it.
Spoofing Definition
Spoofing is a misleading apply the place cybercriminals impersonate one other entity or supply, typically with malicious intent. It could contain varied strategies corresponding to forging e mail addresses, manipulating caller IDs or creating counterfeit web sites to trick people or programs into believing the spoofed entity is authentic. These misleading ways result in unauthorized entry and knowledge theft.
For instance, say you recurrently obtain emails from Amazon.com. A spoofer might disguise an e mail by altering the e-mail handle to “Amaz0n.com” to trick you into sharing your login info with that handle.
How Does Spoofing Work?
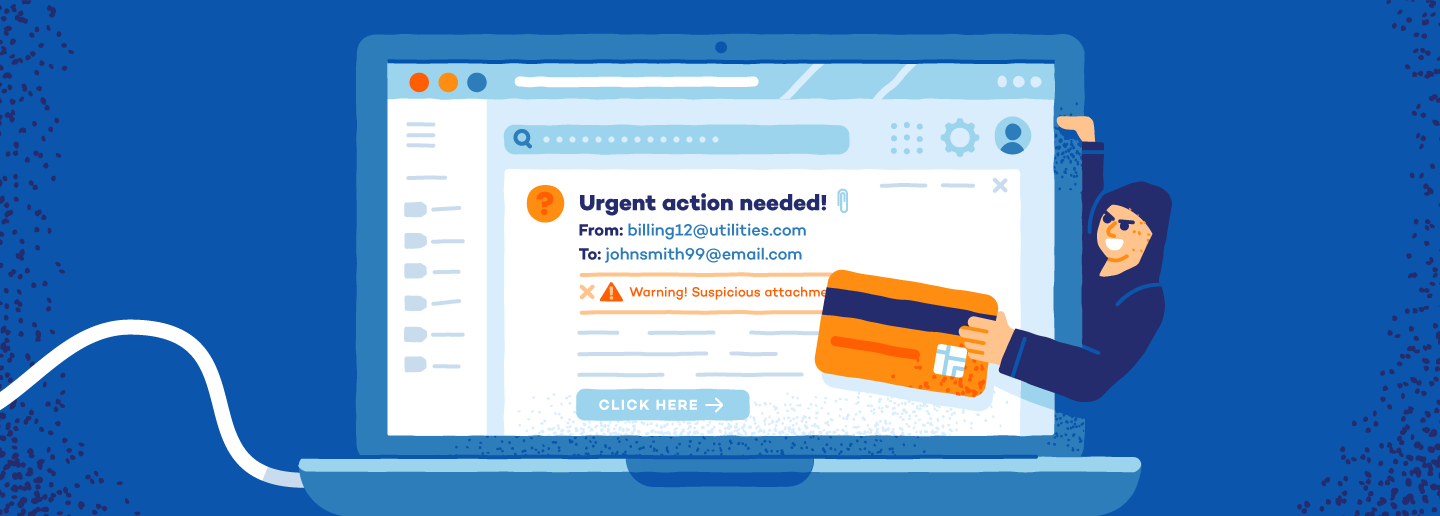
Spoofing operates on a twin technique: the creation of a misleading façade, corresponding to a counterfeit e mail or web site (also called the spoof), coupled with social engineering, which persuades people to take sure actions.
For instance, think about receiving an e mail purportedly from a widely known on-line retailer, attractive you with a tempting low cost supply. The e-mail (the misleading façade) seems genuine, full with the corporate’s brand and branding. Wanting to seize the chance (the social engineering aspect that manipulates your feelings and wishes), you click on on the offered hyperlink, solely to land on a counterfeit web site designed to seize your cost info.
The implications of spoofing might be extreme, main to varied dangerous outcomes. Victims might expertise unauthorized entry to their accounts or delicate info, leading to identification theft, monetary loss or privateness breaches. Moreover, spoofing assaults can compromise the integrity of communication channels, facilitating the unfold of malware, phishing scams or different malicious actions.
Spoofing contains a variety of assaults, from easy e mail and web site tips to advanced technical manipulations involving IP addresses, ARP and DNS servers.
10 Sorts of Spoofing
Spoofing is available in many varieties, and it’s vital to concentrate on the completely different assaults chances are you’ll encounter. Under are some frequent kinds of spoofing and tricks to forestall spoofing:

1. Caller ID Spoofing
Caller ID spoofing is a misleading apply the place callers manipulate the data displayed on the recipient’s caller ID to disguise their true identification and make it seem as if the decision is originating from a unique telephone quantity or entity.
Scammers typically use this system to trick people into answering calls by displaying acquainted or authentic telephone numbers, corresponding to these belonging to banks, authorities companies or trusted contacts — when in actuality, the caller’s true identification could also be fraudulent.
Most scammers use Voice over Web Protocol (VoIP) to carry out caller ID spoofing. VoIP helps scammers create a practical telephone quantity and caller ID title. When somebody solutions the telephone, the scammer will attempt to deceive them into revealing private info.
The best way to forestall it:
- Make the most of name blocking or caller ID spoofing detection apps or providers supplied by your telephone provider or accessible for obtain to assist establish and block suspicious calls.
- Train warning when answering calls from unknown numbers, particularly in the event that they declare to be from acquainted organizations or people. Double-check with the group they’re claiming to be from.
- Chorus from offering private or monetary info over the telephone except you initiated the decision and are assured within the different social gathering’s authenticity. Official organizations will sometimes not request delicate info over the telephone.
- Look out for caller ID that claims “911.” Spoofed caller IDs typically present up as “911 Emergency” as a substitute of the spoofer’s actual telephone quantity.
2. Web site Spoofing
Web site spoofing is when somebody creates a pretend web site that appears like an actual one to trick individuals into considering it’s authentic. The pretend web site might have an analogous design, brand, and internet handle to the actual one, however it’s managed by scammers who use it to steal private info or unfold malware.
Usually, the copycat website’s URL handle shall be related sufficient to a authentic website so it seems actual at first look.
The best way to forestall it:
- Test the URL earlier than clicking. In case you’re suspicious a few hyperlink, hover your mouse over the hyperlink. A URL handle will pop up within the backside left nook of your window so you may see the place the hyperlink will take you earlier than you click on it.
- Test the handle bar to confirm the web site is safe by in search of “https://” earlier than the URL. This means encryption and safety in opposition to cyberthreats. In case you land on an internet site that begins with “http://” (with out the “s” on the finish), shut the window shortly.
- Use a password supervisor, as they need to not autofill login credentials on spoofed web sites. In case your beforehand saved credentials aren’t autofilled, it might point out a spoofed website.
- Search for the lock image or inexperienced bar subsequent to the URL, indicating a safe connection.
3. E-mail Spoofing
E-mail spoofing is a fraudulent approach the place attackers manipulate the sender’s e mail handle to make it seem as if the e-mail is coming from a trusted supply, corresponding to a good group or particular person. In actuality, these emails are from a malicious actor. This misleading apply is often utilized in phishing assaults to trick recipients into disclosing delicate info or taking dangerous actions.
The best way to forestall it:
- Test for any discrepancies or similarities with identified addresses and ensure with the sender should you’re unsure.
- Keep away from opening attachments from unknown or suspicious senders, as they could include malware.
- Use two-factor authentication so as to add one other layer of safety in opposition to spoofing assaults in your units. It’s vital to notice that it’s not utterly foolproof, so remember to pair it with good cybersecurity habits.
- Discover the sender’s contact info on-line to verify authenticity and search suspicious e mail contents on Google for potential scams.
- Report suspicious emails as spam to keep away from clicking on any malicious hyperlinks or attachments by mistake.
4. IP Spoofing
IP spoofing is when an attacker fakes their IP handle to trick a system into considering they’re another person. They use this to cover their identification, launch assaults or achieve unauthorized entry to networks.
The best way to forestall it:
- Allow IP handle validation: Utilizing mechanisms like SEND or DAI helps be certain that units on a community use real IP addresses and should not being impersonated by attackers. Configure these safety features in your community units. Particular steps might differ relying on the gadget and its configuration interface, so search help from a educated community administrator when you have questions.
- Deploy encryption protocols corresponding to IPsec to safe community communication.
- Make the most of sturdy and distinctive passwords for community gear.
- Allow firewall and intrusion detection programs.
- Usually monitor community site visitors for suspicious exercise.
5. DNS Server Spoofing
Area Title System (DNS) spoofing sends site visitors to completely different IP addresses and is commonly used to deliver guests to malicious web sites. Scammers obtain this by changing the IP addresses saved within the DNS server with the malicious addresses they need you to make use of. As a result of it alters your saved knowledge for malicious functions, DNS spoofing is also called cache poisoning.
The best way to forestall it:
- Use DNSSEC (Area Title System Safety Extensions) to authenticate DNS responses.
- Implement DNS filtering options to dam malicious domains and forestall DNS spoofing assaults.
- Usually replace DNS server software program to patch vulnerabilities.
- Make the most of VPN (digital non-public community) providers to encrypt DNS site visitors and shield in opposition to DNS spoofing.
- Confirm web site URLs by in search of “https://” and double-checking the area title earlier than getting into delicate info.
6. ARP Spoofing
Handle Decision Protocol (ARP) spoofing is ceaselessly used to change or steal knowledge for in-session hijacking. It’s additionally known as ARP poisoning or ARP cache poisoning. Scammers normally do that by linking their media entry management to an IP handle to allow them to intercept knowledge initially supposed for another person.
The best way to forestall it:
- Implement ARP spoofing detection instruments or safety options that may establish and block suspicious ARP packets.
- Configure packet filtering guidelines on community units — corresponding to routers or firewalls — to dam or filter out ARP packets from unauthorized sources.
7. Textual content Message Spoofing
Textual content message spoofing is a misleading apply the place somebody manipulates the sender’s telephone quantity utilizing on-line providers or software program that enables them to ship textual content messages with a solid sender ID. Utilizing this software program permits the sender to disguise their identification and probably trick the recipient into believing the message is from a trusted supply when it could be a textual content message rip-off.
The best way to forestall it:
- Be cautious of sudden messages from an unknown sender or with suspicious content material, and chorus from clicking on any hyperlinks or offering private info.
- Double-check the sender’s telephone quantity or alphanumeric sender ID to make sure it matches identified contacts or trusted sources earlier than responding or taking motion.
- Keep away from sharing private info corresponding to passwords, account numbers or verification codes through textual content message — particularly if the request appears uncommon or sudden.
- Allow spam filters or blocking options offered by your cell provider or messaging app to filter out suspicious textual content messages and forestall potential textual content message spoofing makes an attempt.
8. GPS Spoofing
GPS spoofing is a misleading approach the place somebody manipulates the GPS indicators acquired by a tool to falsely report its location. This enables the spoofer to trick the gadget into believing it’s positioned in a unique place than it really is.
GPS manipulation can be utilized for varied functions, corresponding to fooling location-based apps or providers, evading geofencing restrictions or conducting cyberattacks that depend on correct location knowledge.
The best way to forestall it:
- Use encrypted GPS indicators, that are tougher for spoofers to control. Utilizing receivers that assist encrypted indicators may also help forestall GPS spoofing.
- Make use of sign authentication, corresponding to receiver autonomous integrity monitoring (RAIM) or space-based augmentation programs (SBAS), which may detect and reject spoofed indicators.
9. Man-in-the-middle (MitM) Assault
A man-in-the-middle (MITM) assault refers to when somebody hacks a Wi-Fi community to intercept internet site visitors between two events. It additionally contains when a scammer creates a replica fraudulent community in that location for a similar goal.
If the assault is profitable, scammers could have the power to reroute delicate info, corresponding to logins or bank card numbers, to themselves. They will then use this info for malicious functions.
The best way to forestall it:
- Make the most of protocols like HTTPS for web sites and SSL/TLS for e mail to encrypt knowledge transmitted between your gadget and servers, making it troublesome for attackers to intercept and manipulate.
- Train warning when utilizing public Wi-Fi networks, as they’re susceptible to MITM assaults. Keep away from accessing delicate info or logging into accounts that require passwords when related to unsecured Wi-Fi.
- All the time confirm SSL certificates when accessing web sites or on-line providers. Make sure the certificates are legitimate and issued by trusted certificates authorities to mitigate the danger of falling sufferer to MITM assaults by solid certificates. Most internet browsers assist you to view the SSL certificates particulars. You’ll be able to normally do that by clicking on the padlock icon subsequent to the URL within the handle bar. Search for an possibility like “View Certificates” or “Certificates Data”.
- Use a VPN when connecting to public Wi-Fi or unfamiliar networks to encrypt your web site visitors and shield in opposition to MITM assaults by securing knowledge transmission.
10. Extension Spoofing
Extension spoofing permits scammers to disguise malware in extension folders. Recordsdata are normally renamed as a textual content doc (e.g., “filename.txt.exe”) and have malware hidden inside. When a person opens the textual content file, they unknowingly run a bug.
The best way to forestall it:
- Confirm extension sources and solely set up browser extensions from trusted sources corresponding to official browser extension shops or respected builders. Keep away from downloading extensions from unknown or untrusted sources to scale back the danger of extension spoofing.
- Maintain all browser extensions up-to-date with the newest variations to make sure they’ve the newest safety patches and protections in opposition to extension spoofing vulnerabilities.
- Overview permissions earlier than putting in an extension. Be cautious of extensions that require extreme permissions or entry to delicate knowledge, as they could be designed for malicious functions, together with extension spoofing.
- Set up and recurrently replace respected antivirus or anti-malware software program in your units. These safety applications may also help detect and forestall malicious browser extensions, together with these concerned in extension spoofing assaults.The best way to Stop Spoofing Assaults
The best way to Stop Spoofing Assaults

There are various issues you are able to do to guard your self in opposition to spoofing assaults. Keep one step forward of scammers with these useful do’s and don’ts:
Do’s
Listed here are some suggestions to bear in mind to guard your self in opposition to spoofing assaults:
- Flip in your spam filter: This prevents most spoofed emails from even reaching your e mail inbox.
- Learn messages carefully: Spoof assaults normally include poor grammar or unnatural sentence construction. In case you see this, it’s an indication that the request is just not protected. All the time double-check that the URL handle of an internet site or the sender’s e mail handle is appropriate earlier than sending delicate info.
- Verify the supply: In case you obtain communication that appears suspicious, it’s greatest to succeed in out to the sender and ensure that the decision or e mail you acquired is authentic.
- Set up cybersecurity software program: Investing in cybersecurity software program is an effective way to guard your self from cybercriminals on-line. In case you suspect that you just’re being spoofed, obtain malware removing or antivirus software program to guard your units from malicious threats or viruses.
Don’ts
Listed here are some issues it’s best to keep away from to guard your self from spoofing assaults:
- Don’t obtain or click on unfamiliar hyperlinks or attachments: If a hyperlink or attachment seems questionable, don’t click on on it. In the event that they’re from a scammer, it seemingly incorporates malware or different viruses which might be harmful to your laptop.
- Don’t reply calls or emails from unknown senders: In case you don’t acknowledge the sender, don’t reply to the decision or e mail. By not speaking with a possible scammer, you keep away from revealing your private info.
- Don’t disclose delicate info: Keep away from sharing private info, like your handle, checking account, or Social Safety quantity. If you must present this info, take additional steps to verify that it’s a trusted supply.
- Don’t use the identical password: Many individuals use weak passwords that scammers can simply guess. Create sturdy passwords and replace them typically to stop scammers from getting a maintain of 1. Additionally, by no means use the identical password for each login.

In case you assume you’ve been spoofed, you may file a criticism on the FCC’s Client Criticism Heart. You may also contact your native police division should you’ve misplaced cash as a consequence of spoofing.
The above prevention suggestions, in addition to different tricks to shield your private info on-line, will provide help to keep vigilant. Make sure to use antivirus software program to safe your digital info and shield your self in opposition to spoofing.



